Cybersecurity professionals use the word “risk” extensively, but it’s a word with multiple meanings that different people may interpret in different ways. What risk means depends on who’s using the word and the context in which it's used. The same applies to “assessment”: is it a review, a measurement, an opinion or a combination of multiple things?

It’s no surprise, then, that the term "risk assessment" means different things to different people and organizations. By breaking down a risk assessment into its basic components and then reassembling it, it becomes clear how it applies to cybersecurity.
Risk and cybersecurity
In cybersecurity circles, we should always use the formal definition of risk to eliminate confusion. But even major security standards bodies don’t agree on a single definition. The term also takes on slightly different meanings even within the same bodies.
- ISACA’s terminology glossary defines risk as “the combination of the probability of an event and its impact.”
- The International Standards Organization (ISO) in ISO 27005 defines risk as "potential that a given threat will exploit vulnerabilities of an asset or group of assets and thereby cause harm to the organization."
- ISO 31000 defines risk as the “effect of uncertainty on objectives” and an effect is a positive or negative deviation from what is expected. ISO further states that “risk focuses on the effect of incomplete knowledge of events or circumstances on an organization’s decision making. This requires a change in the traditional understanding of risk, forcing organizations to tailor risk management to their needs and objective.”
- The German Federal Office for Information Security defines risk as “the prediction of possible damage, often based on calculation, in a negative case (danger), or in a positive case a possible advantage (chance).”
- NIST SP800 39 defines risk as "a measure of the extent to which an entity is threatened by a potential circumstance or event, and typically a function of i) the adverse impacts that would arise if the circumstance or event occurs; and ii) the likelihood of occurrence."
- NIST SP800-39 further qualifies information system-related security risks as "those risks that arise from the loss of confidentiality, integrity, or availability of information or information systems and reflect the potential adverse impacts to organizational operations (including mission, functions, image, or reputation), organizational assets, individuals, other organizations, and the Nation."
While definitions differ, it’s important not to let them wrap you around an axle. When it comes to risk management, organizations should leverage and apply them to the framework they use. And assessments should take account of overall business strategies and directives as they apply to information, not just the protective controls applied to protect it.
People, process and technology… tried and still very true
For more than three decades, information or cyber risk management has often been associated with three parameters; people, process and technology. Cybersecurity risk assessments that don’t consider all three elements are incomplete and result in flawed assessment recommendations. By way of analogy, imagine a three-legged stool with one or two legs missing.
Challenges do arise when applying the methodology, though. The stool analogy sounds simple, but who are the people? Are they IT staff, cybersecurity staff or someone else? What is the process? All processes aren’t equal, and more to the point, which one is “best” depends on the specific organizational context. The same goes for technology. There are fantastic tools that may be wrong for your situation.
Risk assessments should study how the business operates and model the risk assessment process to those unique dynamics. A three-tiered approach, with each tier focused on a specific set of responsibilities and knowledge, helps address multiple challenges.
The three-tiered model
This model sounds simple. And it is, until you consider the organization’s internal and external influences. If we include those, the model expands as depicted in Figure 1. This figures in some of the complexity that cyber risk assessment include.
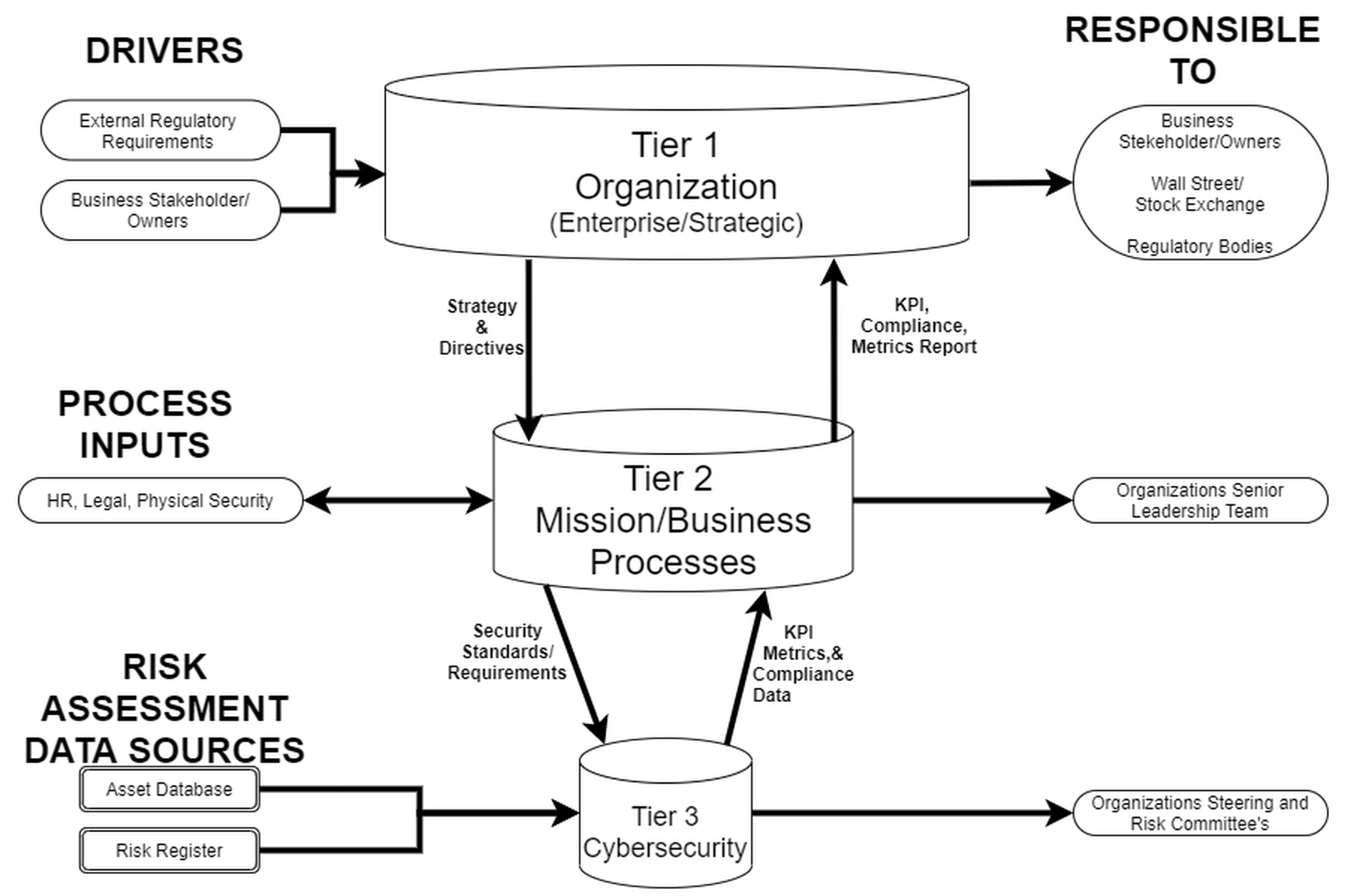
The management responsibilities in each tier are:
- Tier 1: at the organizational level, focus on setting business direction, goals and strategy to satisfy company stakeholders, the stock market (if applicable) and external regulatory requirements (where applicable). Decisions made at this level are rarely automated and depend on people (management), who make decisions to support growth and the continued operation of the company. These decisions include issuing directives to protect information, electronic and other types.
- Tier 2: the business process and mission level is based on knowing the strategic direction set in tier 1 and understanding the information leadership requires. It assures all is well and focused on the business. It articulates what information is needed and how different business unit requirements support and benefit from cybersecurity programs and initiatives. This level defines actions and programs that must be implemented and managed to satisfy their constituent management. Tier 2 defines the cybersecurity standards that tier 3 must implement and manage, but tier 2 doesn’t tell tier 3 how to do it or what technology or processes to use.
- Tier 3: including IT and cybersecurity, is responsible for implementing tier 2 requirements, managing them and providing required metrics data back to tier 2.
The way risk organizations assess and manage in tier 3 is vastly different from tiers 1 and 2. Why? Because each tier is the responsibility of a different level of management within the organization.
Organizations that realize they need a risk management program (which is really all of us) define an enterprise risk management program (ERM) – they may call it something else, but it’s a risk management program that addresses risk throughout the company. In most organizations, the ERM documentation contains relatively little information about managing cybersecurity risk, as the language becomes very technical very quickly. Remember, leadership at the organizational level – i.e. the board and C levels – defines and monitors the ERM. Since these people aren’t typically cybersecurity experts, ERM documentation mandates the creation of a management policy and supporting program that includes cybersecurity risk management (CSRM) that reports risk metrics to the ERM program, the senior leadership team and the Board.
This means that the ERM and CSRM touch at level 2. Because of this, simply assessing cybersecurity risk at the IT level provides a limited and incomplete assessment unless it considers the organization’s strategy, the processes, and the information security management standards created in tier 2 that apply to tier 3.
A cybersecurity risk assessment doesn’t necessarily mean a full-blown enterprise risk management assessment is a requirement. It simply means the cybersecurity risk assessment must be aware and take account of the impact, constraints and requirements associated with decisions and actions made elsewhere in the organization.
This three-tier approach to cybersecurity risk management, which we employ at Optiv, provides and assures organizations that the results of the assessment will improve risk communication, support improved risk reduction and reduce risk management costs over time.
Author Stuart Broderick is an Optiv Risk and Compliance Advisory Services Practice manager at Optiv Security. Read more Optiv blogs here.




