As the cybersecurity threat landscape is evolving so is the way we need to look at those threats. The drumbeat of new breaches is continuous. If you read the news, you would be led to believe that there is only one major tactic the attackers leverage in an INCIDENT against their targets. That is simply not the case, and we need a new way to describe and track these events.

The term ALERT and EVENT need to be clearly defined. Today SOC teams use many different technologies to detect threats. Many large customers have 30 or more security technologies in their defense in depth architecture. Every one of those technologies generate their own specific ALERTS. It is the job of the SOC analyst to review these individual alerts and correlate and combine them into EVENTS. It takes an experienced analyst to write rules to connect the different ALERTS they are seeing into EVENTS or to deduplicate big number of the same ALERTS to a single EVENT.
Attackers know this is a manual time-consuming process. They leverage multiple tactics to overwhelm the SOC analysts with ALERTS from their security tools. For instance, the attacker may leverage a known exploit to generate numerous IDS events. If they are successful, this creates a huge distraction for the SOC team.
While they are dealing with these IDS events, the attackers may have already established a foothold in the environment through a brute force login to one of their critical servers. Next they can scan the internal network from that critical server. If they find another server in the environment with critical data in a SQL database they can compromise it and run a SQL dump command. This puts the entire contents of the database into a file that can be exfiltrated through at DNS tunnel they create to an external IP address.
This is a very simple example of what happens in an INCIDENT. Multiple events need to be correlated to the incident. Here is a simple hierarchy:
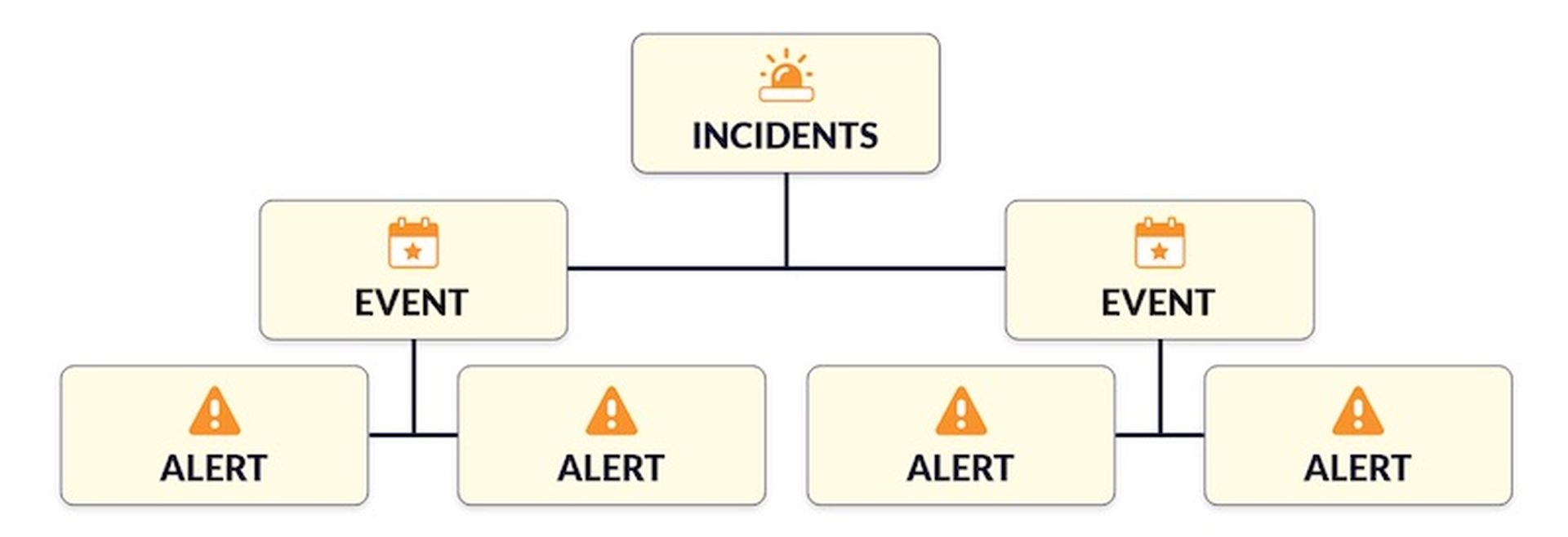
With the sheer number of ALERTS we need to look at how we can leverage technology to help in the classification and correlation to improve the effectiveness of the SOC. Artificial Intelligence and Machine Learning leveraged across this data set can be a very powerful tools.
- Supervised Machine Learning – able to detect previously unidentified files, domain names, and URLs. This is the data commonly found in ALERTS.
- Unsupervised Machine Learning – develops baselines of normal behavior for networks, devices, and users. This can detect EVENTS within the customer network by correlating and combining ALERTS.
- Deep Machine Learning – looks at the landscape of threats in the entire environment and looks for connections. Able to correlate EVENTS into INCIDENTS.
The Machine learning can also help score an event or an incident. When the security analysts review open incidents, this allows them to choose the highest priority incident, and respond immediately.
Leveraged correctly they have the potential to identify connected threats faster so the SOC Analyst can focus on remediation rather than correlating alerts for detection and move from a reactive stance to a proactive one in the process.
Brian Stoner is VP of service providers at Stellar Cyber, which develops a next-gen security operations platform that provides high-speed, high-fidelity threat detection and response across the entire attack surface. Read more Stellar Cyber guest blogs here.




