Most of your customers may think that their native email security or secure email gateways (SEGs) are preventing phishing emails from reaching users’ inboxes. Unfortunately, threat actors are adapting quickly and changing their tactics, often staying a step ahead of security teams. They are increasingly launching more sophisticated attacks, leveraging platforms like social media to mine data and fine-tune their messaging to get phishing emails into inboxes.
While attacks by these crafty threat actors come in several flavors, a common one that has been observed and is increasingly prevalent is an offer to share a document or, similarly, an urgent directive to act on a document.
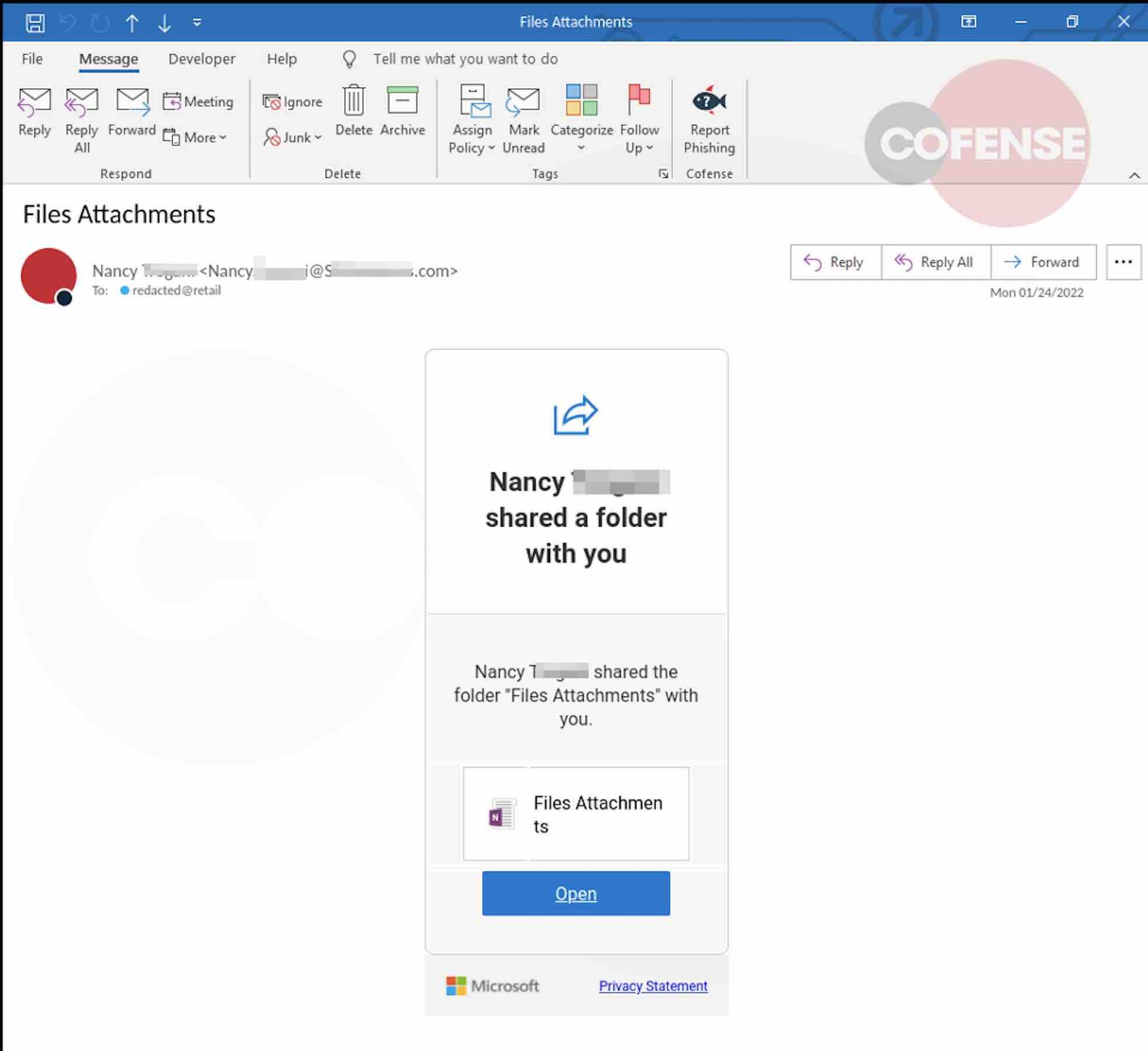
The user is presented with a legitimate-looking login page for a trusted brand such as Microsoft Office 365. These templates can be perfect facsimiles. A trained user will spot a problem with the URL – that it does not match the brand. But many users are moving too fast or are distracted. The phish works.
Why are today’s credential harvesting attacks regularly evading costly controls? Threat actors either mimic brands by creating fake pages, or they create accounts on these legitimate services.
This approach is often effective because of the way SEGs work. For one thing, SEGs filter based on whether a URL has been flagged or placed on a deny list. Other reasons why phish stump controls include the fact that SEGs sample from active, ongoing attacks while phishing attackers wage campaigns quickly, and are ended before they can be profiled. Also, SEGs guard against high-volume, spammy messages, while phish are lower volume and often more targeted. SEGs are particularly challenged when attackers spoof legitimate businesses.
SEGs perform well enough for known threats but they start to struggle with unknown threats and newly stood-up campaigns that may be as short-lived as a few minutes. And, if a URL is not on a known-threat list, a SEG will typically deliver it.
What’s really needed is the ability to examine the URL from a technology standpoint.
SEGs also struggle with business email compromise (BEC) attacks. These attacks often contain no flagged keywords, instead using regular language. SEGs can’t stop these if the keyword or other filters don’t alert. A human may notice the request from a fellow employee is coming from a non-work domain, for example, but SEGs aren’t designed to catch this.
What is needed to detect BEC with technology is the ability to read the content of an email and understand it. Characteristics such as the brand impersonation details must be discerned, as well as the email address and name, and the information within the header and email body.
For example, users viewing an email will not visually detect the presence of embedded code. But when the code behind that message is examined, we can detect specialized HTML and CSS styles that can hide words that normally trigger a SEG alarm – words such as ”Password” and “Expiring.” Obviously designed to bypass SEGs, MSPs need additional technology to prevent users from being exposed to malicious emails.
Last, threat actors may insert a CAPTCHA in between the initial email and another redirect to a login page. Can a traditional SEG identify the photographs with the traffic lights? And the ones with the train? No. But by using computer vision and AI, specialized technology can emulate human response to investigate CAPTCHA challenges. AI complements SEG technology by affording more data points to determine if an email is a phish.
MSPs can take heart. Modern anti-phishing technology that uses visual AI to detect and learn from real-world phishing attacks can stop what native email security and SEGs usually can’t. Contact our team to learn more about Cofense Protect MSP. Book a demo to see how you can provide advanced phishing protection to keep your clients safe from today’s most sophisticated phishing attacks.
Rich Keith is senior product marketing manager at Cofense. Read more Cofense guest blogs here. Regularly contributed guest blogs are part of MSSP Alert’s sponsorship program.




