
The Right of Boom security conference for MSPs is under way in Tampa, Florida. Both MSSP Alert and ChannelE2E are on-hand to cover the event. Keep checking this blog for ongoing updates from the event, which is hosted by Andrew Morgan -- founder of The Cyber Nation and host of The CyberCall.
Here's what we've heard from the event so far:
1. Can Your MSP Really Survive a Cyberattack? We raised and explored that topic ahead of the event. Among our areas of concern: What percentage of MSPs are really qualified to offer MDR (Managed Detection and Response), and how many of those MDR-focused service providers actually offer credible response capabilities? We'll be seeking answers at the event.

2. Top 10 Cloud Security Risks MSPs and MSSPs Need to Mitigate: This topic surfaced during a pre-conference workshop led by Beau Bullock of Black Hills Information Security.
3. MSP Ecosystem Embraces Physical and Virtual CISOs: Full-time chief information security officers, virtual CISOs and associated technology startups are popping up across the MSP software industry — leading a multi-year journey that is starting to deliver improved MSP industry security and enhanced risk mitigation. It's a safe bet the vCISO trend as well as actual CISOs -- including Datto's Ryan Weeks -- will be on hand at the conference.
Thursday Keynotes & Content at Right of Boom Conference

4. Laggards In This Journey Get Left Behind: That's the key takeaway from Wes Spencer, who called on the MSP sector to move together, continue to shift right and make sure no MSP gets left behind in the cyber journey -- especially as MSPs begin to master detection and extend their focus to effective right.
5. Wes Spencer Joins Rewst: Details about Spencer joining Rewst are here from ChannelE2E. Rewst is a Robotic Process Automation (RPA) software startup focused on MSPs.

6. MSP Security Progress: In the past three years, the MSP industry has made 10 years of progress, Morgan asserted. I agree.
7. Blackpoint Cyber CEO Jon Murchison: Most of the initial targeting involves RDP being open to the Internet, an unpatched firewall or phishing. You'd be surprised how many Exchange Servers remain unpatched. Also, be careful of rogue RMM (remote monitoring and management) installs and related free trials that may not be secure, he noted.

8. DMZs Are Dead: Move to the Zero Trust Model for a proper path forward, Murchison said.
9. Get to Know the Center for Internet Security: A key name to know is Phyllis Lee, senior director for controls at the Center for Internet Security. Lee pointed out that MSPs need to really understand effective cyber hygiene to maintain a proper posture, and be aware of where you data is going, records you care about -- and the fact that your network ends at your employees' and partners' fingertips. Also, read up on the Microsoft 365 security guidance from CIS, Murchison said.


10. The Year of Supply Chain Vulnerabilities and Mass Exploitation: Here, guest speakers John Hammond of Huntress and Jennifer VanderWier of F1 Solutions emphasized that MSPs have to look beyond their RMM to really analyze the security of every toolset the test/adopt. In F1 Solutions' case, the MSP created a standardized list of security questions that team members ask their tool vendors. And in many cases, F1 Solutions will ask multiple sources at a software company about their cyber posture -- to see if all the statements match.
11. Ten Security Vendors MSPs Should Ask Their Software Suppliers: Thank you to VanderWier and Hammond for the list.
Friday Keynotes & Content at Right of Boom Conference

12. The Irony of Automation: A great paper, recommended by keynote speaker Sounil Yu, CISO & head of research at JupiterOne.
13. Resources from Sounil Yu: Thank you to Kyle Jackson, senior program manager at ConnectWise, for that high-value link.
14. The Cyber Defense Matrix: The grid is below. For more info, check out Sounil Yu's website. The site is required reading for MSPs and MSSPs. The grid is all about helping organizations to map and improve their security controls.
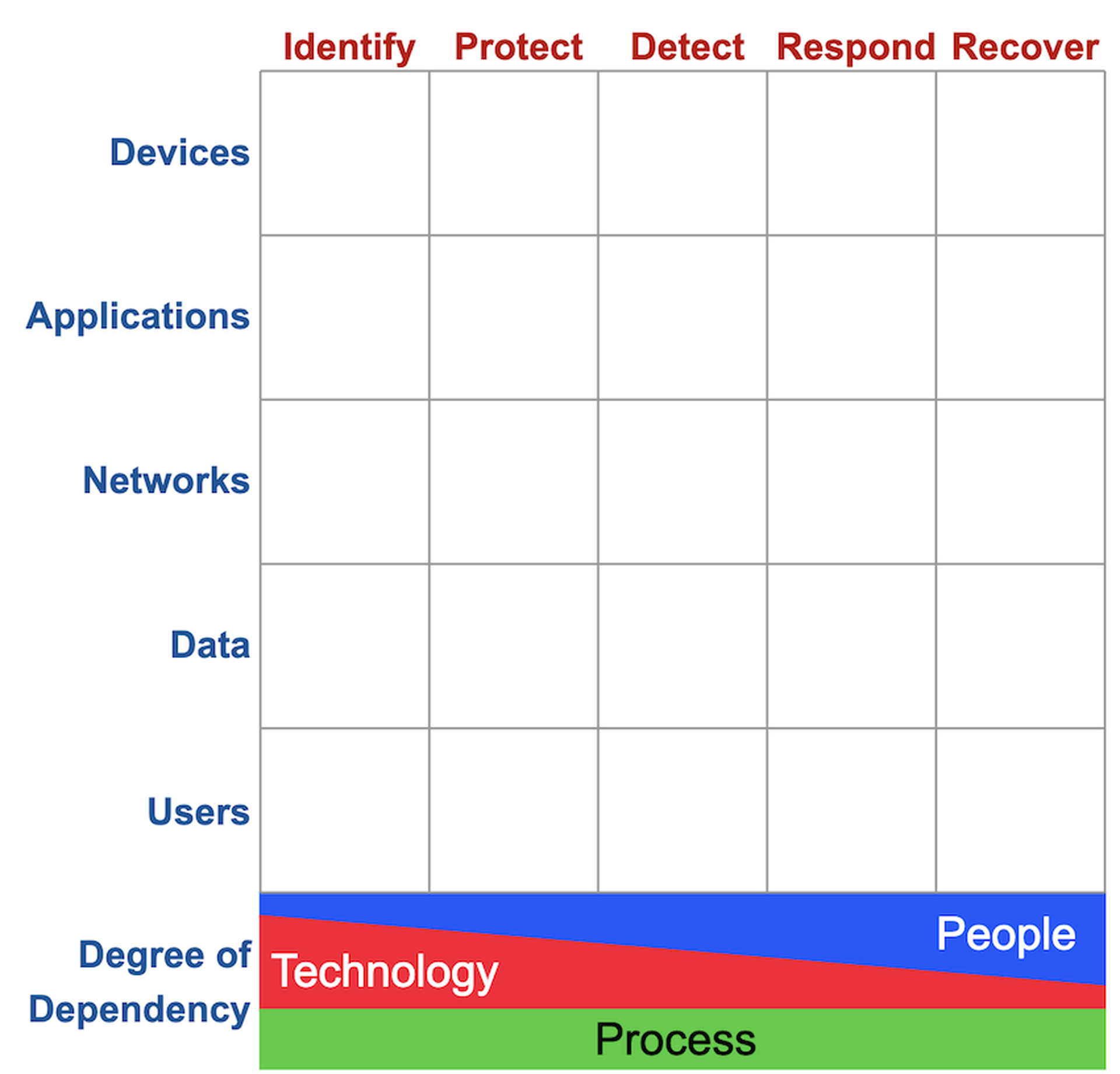
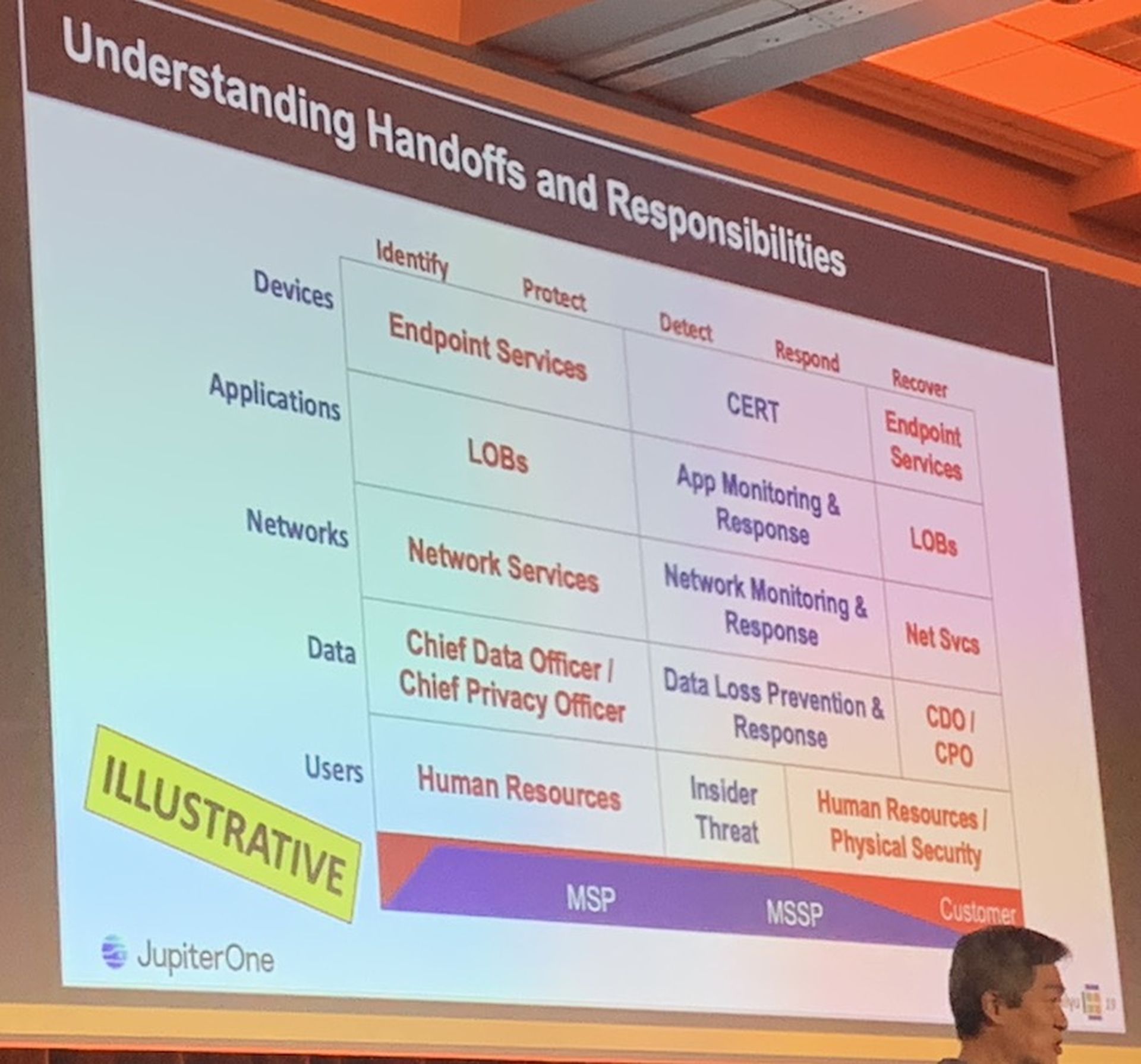
14. The Cyber Defense Matrix - Where MSPs and MSSPs fit: What's the difference between an MSP and an MSSP? Generally speaking, I often say that MSPs are in the shallow-end of the security pool and also offer general purpose IT support. MSSPs are in the deep-end of the security pool and focus purely on security. That's my spin. But Yu gets even more granular by mapping out MSP and MSSP capabilities in the Cyber Defense Matrix. Note: Yu's mapping is meant to be a general perspective rather than any type of official, firm guide for the services that MSPs and MSSPs generally offer. Here's the mapping:
15. Additional News Updates: Keep checking this blog for more updates. And if you'd like to meet or say hi at the conference, then send me an email (Joe.Panettieri@CyberRiskAlliance.com).




