From healthcare and big tech to finance and government, ransomware gangs are inflicting heavy damage. Many of these attacks have heightened attention around third-party risk and the security obligations of MSPs who play an important role in meeting multiple customers’ IT needs.
It’s no coincidence that vulnerable third parties were behind some of the most damaging cyber attacks in the last few years. More than a dozen of the biggest ransomware attacks on health providers in 2022 each impacted over 1 million records, with half of these incidents stemming from third parties.
The REvil ransomware attack on IT provider Kaseya in 2021 is believed to have directly impacted between 50 to 60 of Kaseya’s customers, even though the company estimates around 1500 downstream businesses were ultimately affected by the breach.
More recent attacks, like the one on multi-cloud provider Rackspace Technology — whose customers include government, education, and financial services groups — is further proof that ransomware actors have intentionally begun targeting MSPs in order to access sensitive data belonging to customers.
The situation has grown increasingly dire, even prompting a joint cybersecurity advisory by the Five Eyes alliance warning about the rising threat of ransomware attacks on vulnerable MSPs and their customers.
The advisory reads:
“Whether the customer's network environment is on premises or externally hosted, threat actors can use a vulnerable MSP as an initial access vector to multiple victim networks, with globally cascading effects. The U.K., Australian, Canadian, New Zealand, and U.S. cybersecurity authorities expect malicious cyber actors — including state-sponsored advanced persistent threat (APT) groups — to step up their targeting of MSPs in their efforts to exploit provider-customer network trust relationships.”
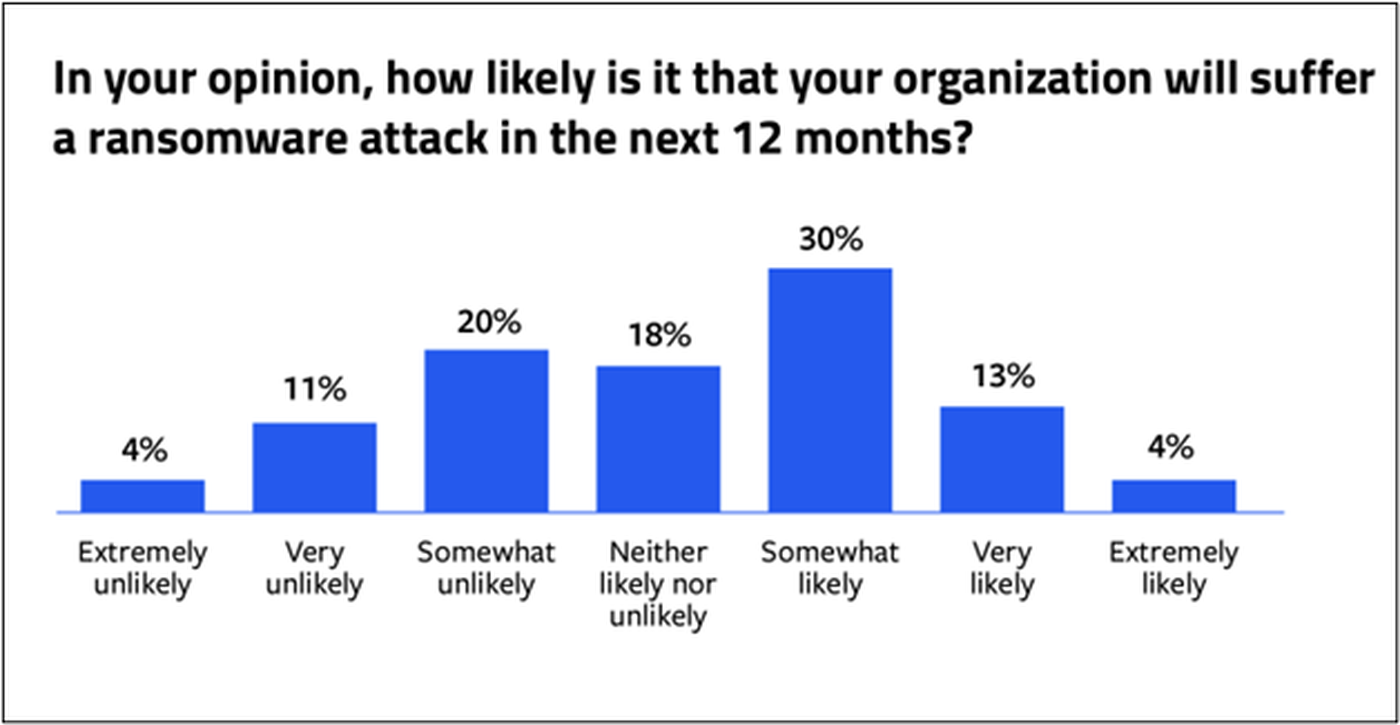
Ransomware: What the Data Confirms
In late 2022, CyberRisk Alliance Business Intelligence surveyed over 200 IT security leaders, administrators and compliance professionals to assess organizations’ ransomware defense capabilities, as well as to gauge current usage and future plans for anti-ransomware solutions.
In addition to providing a snapshot of what organizations are dealing with, the survey data carries big implications for MSPs looking to assure their customers that their data and personnel are protected against ransomware.
Nearly one in four (23%) respondents reported their organization had experienced one or more ransomware attacks in the past 12 months. Almost one out of three (31%) said attackers succeeded in gaining access to their systems, encrypting files, and demanding a ransom — which 2% of victims paid.
This year’s forecast looks no brighter: 47 % believe their organization is likely to suffer a ransomware attack in 2023, and that ransomware attacks are now so inevitable they’ve become a “trend.” Their fears are further exacerbated by reports alerting them to attacks focused specifically on their industry sectors, including healthcare, education, financial services, airports and the public sector.
Larger Attack Surface
Respondents recognize that with the increased number of threats comes a greater likelihood of an attack. They attribute this increased risk to widened surface areas, more external systems connected to organizations’ networks, remote workers, and access points out of the scope of their security protection.
These findings echo those of a previous survey conducted by CRA in November 2022, in which 39% of respondents attributed the cause of a breach to a business partner, subcontractor, or IT service provider. Respondents believe their increased dependency on vendors (including manufacturers, suppliers, and subcontractors) as well as lack of visibility into third- and fourth-party partners have vastly increased their exposure to attacks.
Not Sitting Still
However, these setbacks have spurred many respondents to take ransomware more seriously. A majority have embraced well-established methods, such as employee security awareness training (83%), formal policies and procedures (66%), network segmentation (60%), and ransomware incident response plans (54%). At least 4 in 10 respondents have purchased ransomware insurance or follow a standardized framework such as NIST.

Backup and recovery (94%) and anti-malware/anti-virus solutions are universal among all respondents’ organizations, with 94% and 93% adoption, respectively. A majority have also implemented endpoint security (87%) and vulnerability management (77%). Additionally, 43% of respondents indicated they have plans to adopt zero trust, making this one of the most popular future enhancements of their ransomware protection strategies.
While most (68%) said they will develop or revise their ransomware incident response strategy to prepare for a future ransomware attack and put more effort into employee training, more than four out of 10 respondents said they will either purchase or upgrade their ransomware protection software.
The Case for MSPs in Fighting Ransomware
Between the Five Eyes joint cybersecurity advisory to MSPs and customer complaints regarding third-party vulnerabilities, one might be led to believe that getting IT needs met through an external provider is asking for disaster. But that is not the case, so long as MSPs heed these warnings and take seriously their role as trustees of customer data.
Below are a handful of actions that the Joint Cybersecurity Advisory recommends MSPs can take to better protect their customers from ransomware attacks:
1.) Apply zero trust methods of least privilege and MFA to customer environments. Service level agreements between MSPs and customers should be grounded on the philosophy of zero trust, which forbids access from being granted to any entity that cannot prove they are who they say they are.
MSPs should recommend the adoption of multifactor authentication (or MFA) across all customer services and products, and additionally implement MFA on all accounts that have access to customer environments. Likewise, accounts that have access to customer environments should strictly adhere to the principle of least privilege, which ensures users are granted only the minimum level of access required to perform their duties.
2.) Implement robust network segregation. Identifying and isolating critical business systems and applying appropriate network security controls can reduce the likelihood of a ‘cascade impact’ across the organization. MSPs are encouraged to review and verify all connections between internal systems, customer systems, and other networks.
Customer data sets should be segregated from each other — as well as from internal company networks — to limit the impact of a single vector of attack. Do not reuse admin credentials across multiple customers.
3.) Enforce routine customer backups and save backups in separate locations. Backing up customer data is critical to building resilience in the event of a ransomware attack, but there’s a right and wrong way to go about it.
One respondent summed up the dangers of the wrong way when they said:
“We are learning about how ransomware bad actors will hack into a disaster recovery system and delete backups before triggering the ransomware, which eliminates the ability of a company to go back to their restores.”
To ensure this doesn’t happen, MSPs should store backups separately and isolate them from network connections that could enable the spread of ransomware. It’s a good idea to store these backups on external media, such as a hard drive for example. In addition to backing up customer data, MSPs should maintain offline backups encrypted with separate, offline encryption keys.
4.) Apply updates and patches. MSPs should implement updates on internal networks, operating systems, and applications on a consistent basis, and as quickly as possible. Customers should ensure that they understand their MSP's policy on software updates and request that comprehensive and timely updates are delivered as an ongoing service.




