Even though zero trust (ZT) doesn’t denote a specific security product, it’s clear that more MSPs/MSSPs are modifying their product offerings to be compliant with and supportive of this security philosophy, which operates on the basis that no actor, system, network or service operating outside or within the security perimeter should be automatically trusted.
Several forces are responsible for the ZT push. Market researchers are optimistic that the global ZT security market will balloon in coming years, with estimates of compound annual growth rates ranging between 14% to 18% by 2030.
The ZT architecture strategy released by the Biden administration in 2021 — and subsequent policies issued by NIST, CISA, and DOD on the subject — have effectively catapulted zero trust to the forefront of public sector digital transformation agendas. Meanwhile, high-profile data breaches such as the hacking of SolarWinds, Okta, and Accellion illustrate the dangers of retaining outdated, perimeter-based security principles that fail to address the complexities raised by cloud services, rapid endpoint growth, and remote users operating beyond the network perimeter.
Even as terms like zero trust architecture (ZTA) and zero trust network architecture (ZTNA) finally enter the mainstream security lexicon, the latest research suggests that many organizations still struggle to understand what is needed to implement it effectively. By tailoring their services to address these challenges head-on, MSPs and MSSPs have a unique opportunity to assist customers on their ZT journey.
Zero Trust: What the Data Confirms
In early 2023, CyberRisk Alliance Business Intelligence surveyed over 200 IT security leaders, administrators and compliance professionals to understand their concerns and strategies for establishing ZT. According to the data, several factors are responsible for shaping these perceptions.
Respondents say the basic ideas behind ZT aren’t difficult to grasp. They understand that rather than protecting the castle’s crown jewels using perimeter-based measures (think of a moat and portcullis), ZT is about locking away every valuable in the castle behind its own separate vault with its own unique key.
Many also recognize the role it would have on the organization’s security posture, with 68% of the opinion that ZT has grown in importance in the past 12 months, and another 44% saying their employer is actively pursuing zero trust through strategic planning or implementation.
ZT makes sense on the surface. However, there’s a whole other part of the iceberg known as “implementation.” And that’s the enigma many struggle to solve. According to CRA survey data, roughly just 1 in 4 respondents (26%) express high confidence that they understand their zero trust framework.
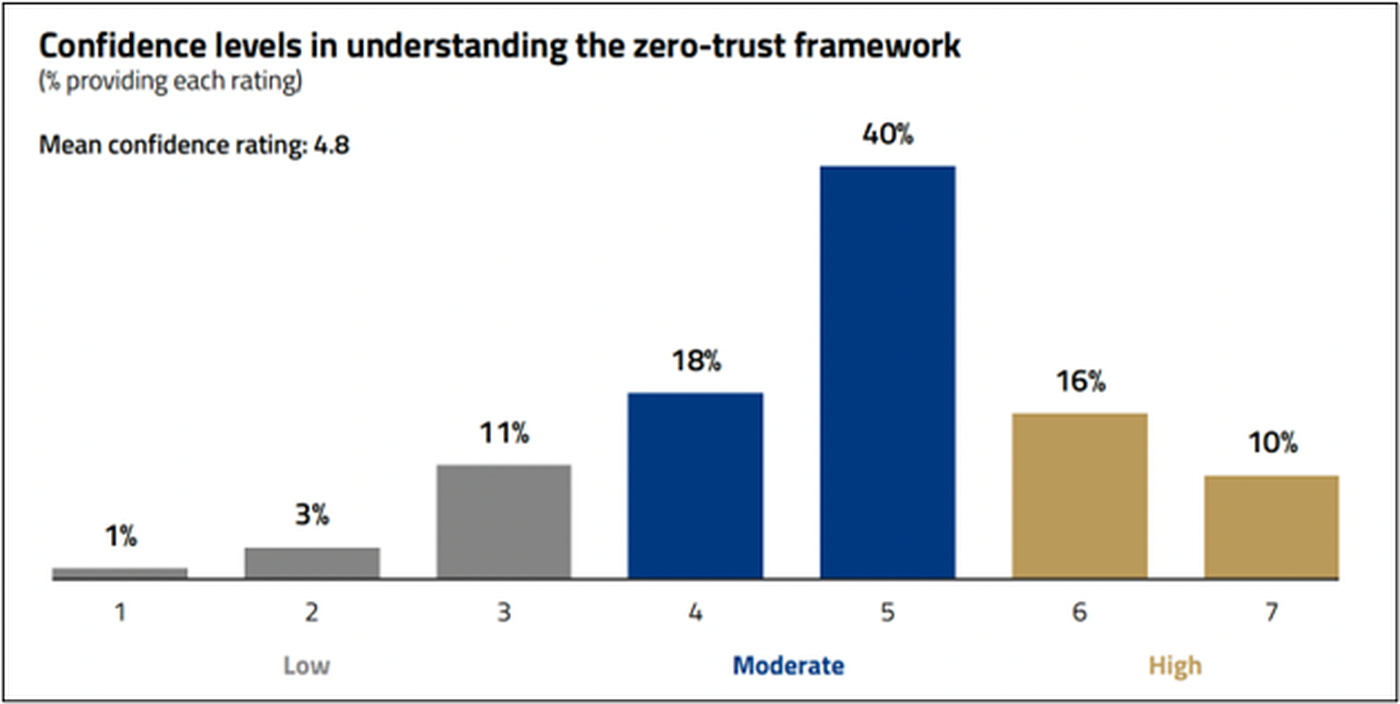
When it comes to putting ZT ideas into practice, organizations tend to buckle under the obligations and demands this entails. One respondent put it this way: “First, we need to train our infosec staff and end users, which will require a good bit of brick laying and describing. Next, we need to actually start locking things down. Again, a tough process. Last, we need someone to look over our shoulder and provide guidance.”
In other words, respondents believe in the power of ZT. But bringing it to life is a significant task that many feel unprepared to conquer on their own.
“Houston, We Have a problem”: Obstacles to Launching Zero Trust
The process of implementing zero trust security isn’t a cakewalk, according to respondents. Approximately two-thirds of individuals who say zero trust plans are in motion expect the resulting implementation will be moderately difficult to pull off. Another 30% go even further, assigning it the highest difficulty rating.
Even respondents who have already implemented ZT concede the experience has been and continues to be challenging. These challenges range from concerns about how ZT will affect the user experience (50%), whether ZT can align to meet business requirements (44%), as well as not having enough staff in place to implement the ZT framework effectively (31%).

All of these are challenges that MSPs and MSSPs are uniquely positioned to help solve. Industry products like CSPM, EDR, XDR, and CNAPPs can be engineered and configured for ZT compliance without compromising on the user experience. Likewise, by collaborating with a MDR provider, organizations can gain access to threat hunters and security analysts steeped in ZT best practices.
MSPs offering vulnerability assessments, pen testing, or backup and disaster recovery can work with customers to make sure these services enhance business outcomes.
Most Common Zero Trust Applications
According to the CRA survey data, respondents are pursuing zero trust in a variety of ways, and for a range of reasons. In just the last few years, we’ve seen organizations shift to cloud-based infrastructure, dramatically expand their data sources and endpoints, and strive to accommodate employees working in the WFA environment.
Respondents’ hopes for zero trust reflect these transformative leaps, as 69% say better data security is their main objective for a zero-trust framework. Half of respondents believe implementing zero trust can improve cloud security, work-from-home security and internet security. Multifactor authentication (84%), identity and access management (75%) and least privilege access (70%) are the most common tools respondents use in the pursuit of zero trust.
On the other hand, just a third of those surveyed say they’ve formalized zero trust policies. And only 18% have dedicated specific personnel for the task of enforcing zero trust policies. In other words, we see an emphasis on ZT technologies over ZT skills and strategic expertise.
A Tectonic Shift in Cybersecurity Calls for Expert Support
Zero trust signals a monumental shift in how organizations secure their data, assets and users. One respondent described it as a “dramatic paradigm shift in security philosophy” that will require strategically reassessing how to secure the entire infrastructure to address challenges of remote or hybrid offices, multi-cloud environments, identity and authentication and rapidly expanding endpoints.
MSPs/MSSPs, take notice. Navigating these treacherous waters will put many organizations far outside their comfort zone. With their depth of skilled specialists and best-in-breed technologies, MSPs can play a critical role in educating customers, influencing the security culture and tailoring their services to support ZT policies while respecting the customer’s business.




