So, here’s the problem: Unknown zero-day threats are just that - unknown. You have no way (besides historical experience) to predict the next vulnerability avenue that will be exploited. You therefore don’t know what will need patching or what extra security layer needs injecting, which ultimately leads to a forecast-costing dilemma as you cannot predict the man hours involved.

The other quandary faced when tackling complex targeted zero days is the skills gap. Staffing a security operations center (SOC) with highly skilled cyber-security professionals comes at a cost and only becomes profitable with economies of scale that a large customer base brings. Coupled with the shortage of skilled cyber-security professionals in the open market, how can you get your SOC off the ground? Could artificial intelligence (AI) level the playing field?
Machine Learning Reality Check
Machine learning and behavioral analytics continue to grow and become synonymous with zero-day threat protection. Is this all hype or is it the new reality? The truth is, it is both. There is a lot of hype, but for good reason: AI works. Big data is needed to see the behaviors and therein the anomalies or outright nefarious activities that human oversight would mostly fail to catch. Delivered as a layered security approach, AI is the only way to truly protect against modern cyber warfare, but not all AI is deterministic and herein lies the hidden cost to your bottom line.
SOC AI-based analysis tools providing forensics are very powerful, but the horse has bolted by the time they are used. This approach is akin to intrusion detection systems (IDS) vs. intrusion prevention systems (IPS). The former are great for retrospective audits, but what is the cleanup cost? This usage of behavioral analysis AI solely for detection is not MSSP friendly. What you need is automated, real-time breach detection and prevention, with prevention being key.
So how do you create an effective prevention technology? You need security layers that filter the malware noise so each can be more efficient at its detection and prevention function than the last. That means signature-based solutions are still necessary. In fact, they are as important as ever as one of the first layers of defense in your arsenal (content filtering comes in ahead at the top spot).
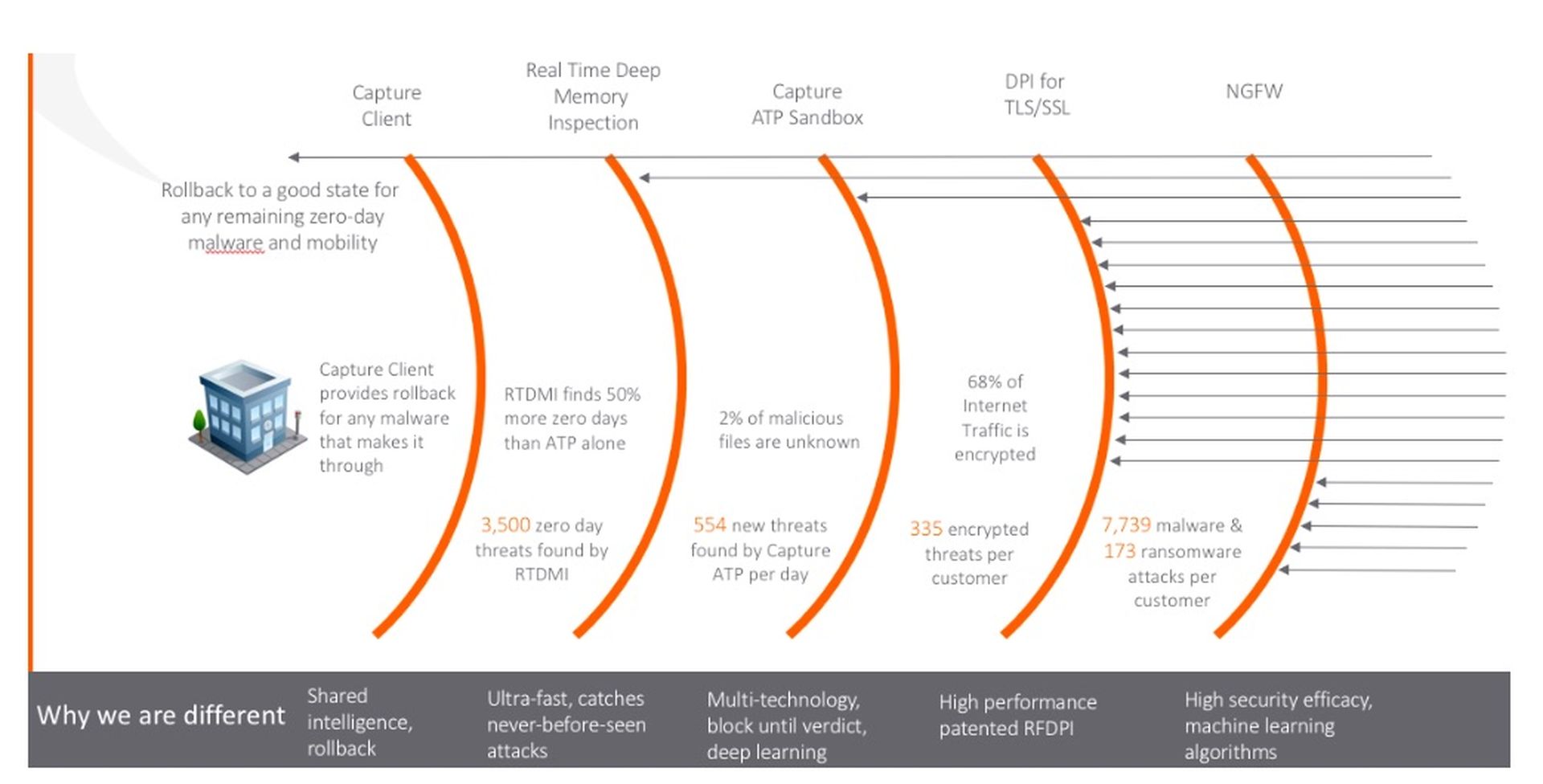
By SonicWall metrics, the ever-growing bombardment of attacks the average network faces stands at 1200-plus per day (check out the SonicWall threat report for more details). When you do the math, it’s easy to see that with millions of active firewalls, it’s not practical to perform deep analysis on every payload. For the best results, you must efficiently fingerprint, and filter everything that has gone before.
What happens at the sandbox layer and aren’t all sandboxes basically the same?
Only by understanding the behavior of the application and watching what it’s attempting to do, can you uncover malicious intent and criminal action. The best environment to do this is a sandbox, but no SOC manpower in the world could accomplish this with humans at scale. In order to be effective, you must turn to AI.
AI understands the big data coming from behavioral analysis, it can adapt the discovery approach to uncover threats that try to hide and once determined as malicious, can fingerprint the payload via signature, turning a zero day into a known threat. It is the speed of propagation of this new, known signature to the protection appliances participating in the mesh protection network that drives the efficiencies to discover more threats. Also, it’s the size of the mesh network catchment area that allows you the largest overall service area of attaches, which helps your AI quickly learn from the largest sample data set.
Luckily, SonicWall has you covered on all these fronts. SonicWall has the largest global footprint of active firewalls. We have the fastest zero-day-to-known-signature generation engine with our Capture Threat Network and the most dynamic multi-engine sandbox on the market. Our recent introduction of the RTDMI engine, which inspects memory in real time, is an important new development, as it can detect and prevent chip vulnerability attaches such as Spectre and Meltdown.
At SonicWall, the mantra of automated breach detection and prevention-layered security is fundamental to our security portfolio and it is how our partners drive predictable operational expenditures in the most challenging security environments. Only via connected solutions, utilizing shared intelligence, can you protect against all threat vectors.
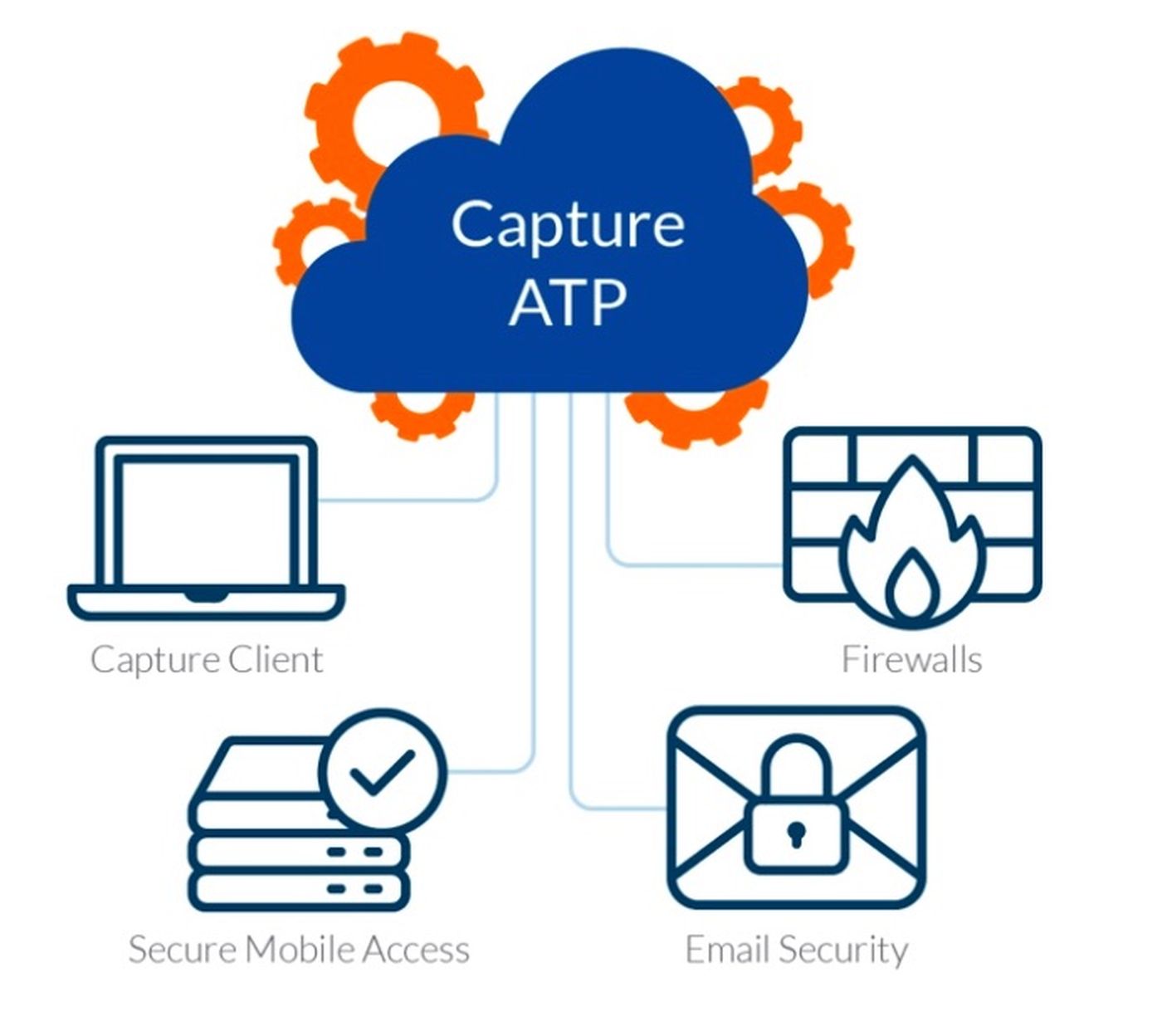
To find out more about how you can operate a “SOC in a box” and explore more about our cost saving features such as remote “zero touch deployment,” visit www.sonicwall.com and ask for a demo.
By SonicWall Sales Engineer James Whewell. Read more SonicWall blogs here.




