I think we should all congratulate each other. We’ve made it three-quarters of the way through one of the longest years in history. The channel community (Partners and vendors) has had to adapt to an uncertain future and learn to thrive in this new world. Unfortunately for us, all the bad actors in the world have been doing the same while congratulating one another for thriving alongside us. While their attack methods have adapted (you can find out a lot more in the Zix | AppRiver 2020 Mid-Year Global Threat Report), the change I find most interesting is the manner in which threat actors attain the means to attack customers.
Let’s take a stroll down memory lane. Ten years ago, in order for a single attacker to launch a malware or phishing campaign, they’d need some serious know how. They’d have to research attack methods that would work for them and their target, develop the malware (not an insignificant task), create web collateral and email campaigns, spin up a hosting environment, and only then would they be able to deploy the campaign. Five years ago, prebuilt templates began to emerge for sale on the dark web. With a TOR Browser and an .onion address, they could shortcut their deployment time considerably. Today, malware and phishing campaigns have gone mainstream. No longer are tools to attack thousands relegated to only those with coding experience or an understanding of the dark recesses of the internet. Today, with a simple browser and a bit of searching, you can find these tools for sale on the clear web.
Phishing Kits For Sale!
If you are anything like me, then you’ve spent the better part of 2020 buying way too much junk from Amazon. Why Amazon? Well, the ability to buy the perfect pen that has hundreds of reviews is just what the doctor ordered when you are stuck at home. Threat actors are no different in their desire to buy only highly-regarded phishing sites. With over 200 different kits to target whichever service they’d like (Excel, Google Docs, DocuSign, Microsoft 365, etc.), the prebuilt fishing sites available for sale on a popular clear web site are easy to download and deploy. Attackers receive these files as a .zip and are ready to deploy to the server of choice (increasingly this server resides on the target platform….hello Azure).
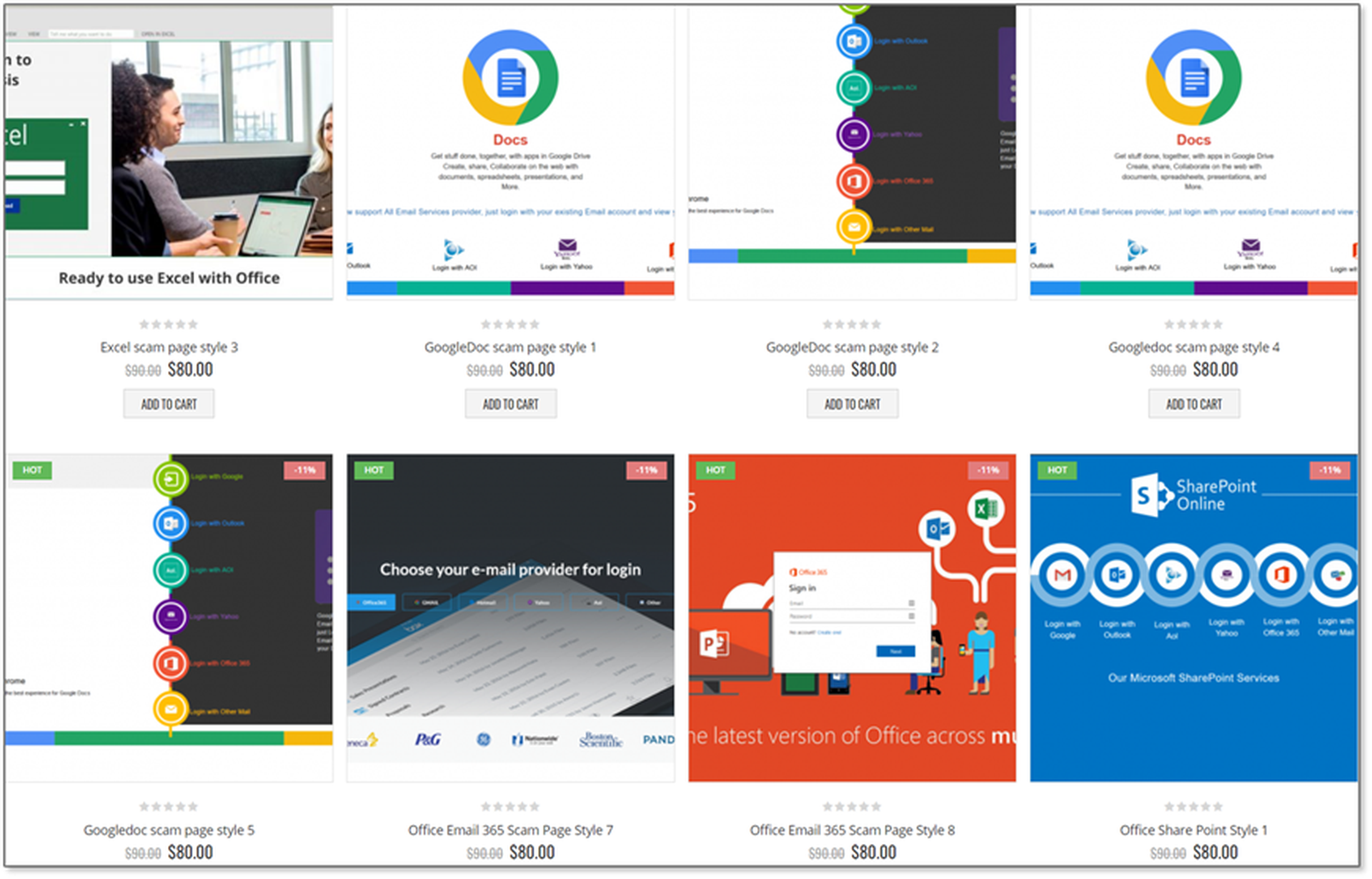
You’ve Done Your Job Too Well!
Over the past few years, you’ve told every one of your customers that their weakest link is their employees - and you are right. You’ve also trained these employees on what to look out for, how to hover over links to see the true URL, and to be suspicious of emails received in the blind. In years past, it was easy to spot a bogus site masquerading as a legitimate site, so training was highly effective. Over the past few years though, attackers have started working with web developers to create highly effective traps for your customer’s employees. Below is a screenshot from one such site. While this example doesn’t have a MSFT URL, increasingly Living Off the Land (LOtL) style attacks that use Azure for hosting make this a difficult-to-spot attack (Azure sites reference MSFT, Windows, etc in the URL). Hovering over menu items appears to link to Microsoft pages, and most notably the background is a looping video similar to what you’d see on most modern MSFT pages. You’ve trained your customer’s users to be suspicious and to be on the lookout for URL’s that don’t make sense, but attackers are growing more savvy.

Malware as a Service
New design aesthetic isn’t the only evolution the bad actors of the world have undergone. While the partner community has been moving from a project-focused approach to one based on recurring revenue, so have malware developers. The discerning attacker now wants post-purchase support on the malware they purchased. They want to be sure that the product continues to get updates and that their purchase is covered. Today, they have all of that and more with options from month-to-month support all the way up to lifetime support. Below is an example of Agent Tesla (one of the most effective remote access Trojans of 2020) in an online store available for purchase. Developers provide post-purchase updates and support where needed, just like you offer support to your customers.

How to Sell More Security Services
As you evolve your strategy to protect your customers, be sure to stay in the know with how attackers are evolving their strategies. This starts with understanding the attacks (you can hear directly from our analysts during this webinar) and ends with modifying your sales techniques to sell more security services. One of the most effective tips I regularly suggest is using data to help you position your managed security services. We help partners accomplish this with a free tool we provide, the Microsoft 365 Security Audit Service. You can see the full presentation I provided to our partners regarding that service, plus more information on the shift to malware purchasing here. If you’d like to have a security audit run for you or one of your customers, reach out to our team at [email protected].
Best of luck out there!




