Employees tend to be bombarded with business communication emails: Microsoft teams messages, internal policy updates, deadline reminders, etc. As a result of loud inboxes, threat actors capitalize on this opportunity to communicate malicious emails, in a bid to harvest employees’ credentials as well as blend in with the noise.
Recently, our Phishing Defense Center (PDC) observed a phishing campaign whereby threat actors impersonate popular brands such as Microsoft and claim “the password for “…” will expire today” as noted below in Figure 1.
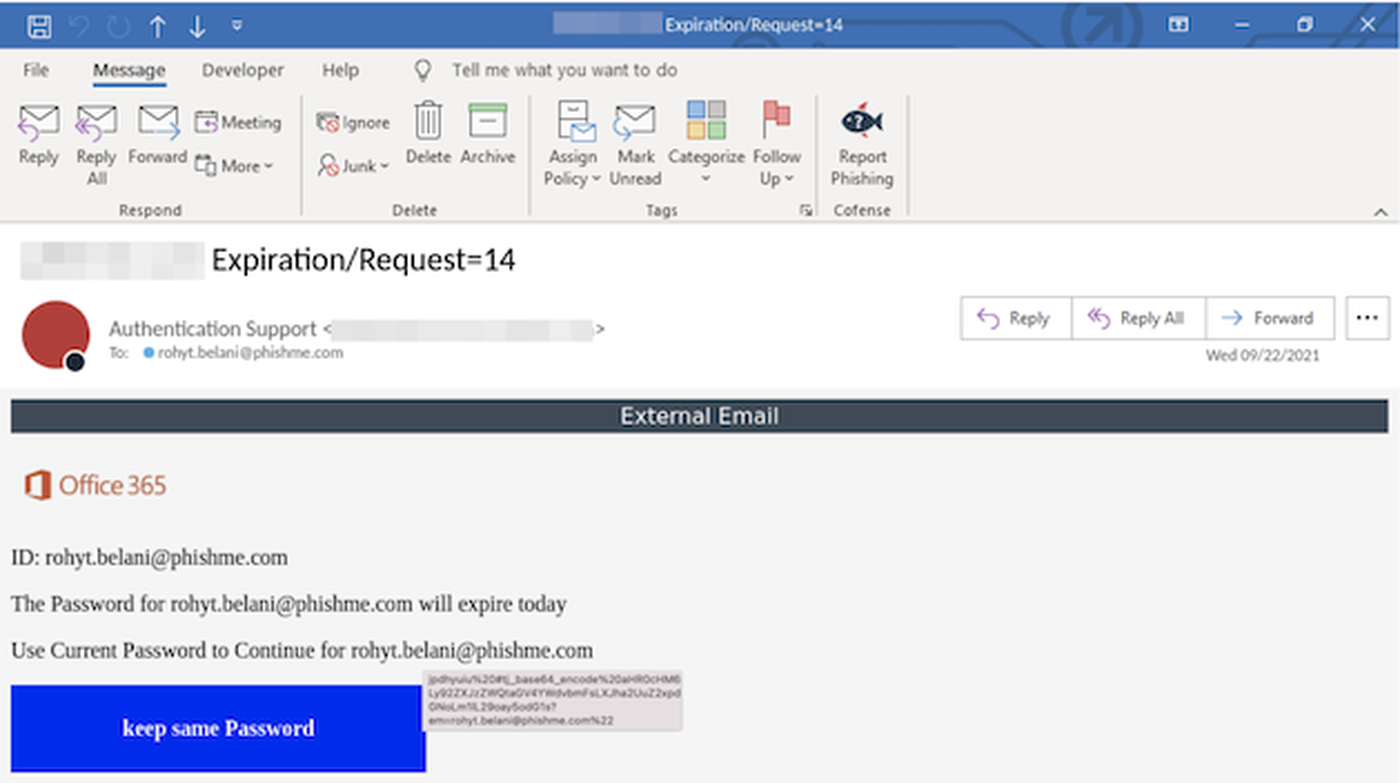
Figure 1: Initial Email
This attack preys on a companies’ password policies. This could include changing it every 30 days or having minimum character requirement. Employees may get legitimate monthly reminders asking them to update their password as it’s expiring soon. As a result, an employee may see this phishing attack and think nothing of it, and begin to engage with the fake request, thinking they’re updating their password as they’ve done so legitimately before in the past.
The text within the subject line in Figure 1: “Authentication Support” gives the impression it’s originated from the (information technology) IT department themselves; again, trying to appear legitimate.
There are no introductory phrases such as “Dear” “Good Morning” “Hello” etc. This indicates a mass email campaign in with the attacker has a purpose-built altering a few variables i.e., “ID” and “email address”. Figure 1 showcases the Microsoft themed brand, evident via the Office 365 image in a bid to deceive the recipient and appear legitimate.
The static IP addresses allow for a high degree of signature-based detection efficacy which is a bonus for the defending side. These static IP sending addresses can be blocked by the end-point detection team.
However, in contrast the sender address in this case is generated dynamically on the fly per instance of the phishing attempt being sent. This has a detrimental effect on the ability to block based on sender alone. In this instance focusing on the static elements of this particular phishing attempt is the best case of action for preventing an attack of this kind from reaching the end user.
Threat actors sometimes use legitimate but compromised top level domain (TLD) names to send out such phishing emails. Searching the (TLD) via open-source-intelligence (OSINT) led us to a legitimate software company based in the United States (US) which was first registered online in 1998. On the other hand, the display name has been spoofed “Authentication Support”; again, socially engineering the recipient into thinking it’s assessed from a trusted source.

Figure 2: Phishing landing page
Should your customer’s employee click on the “keep same Password” hyperlink in Figure 1, they would be redirected to a fake Microsoft login page. The image above in Figure 2 is what they’d see. It looks perfectly legitimate with all functionalities a legitimate Microsoft login page would have. Should they have provided their credential’s the web page would seamlessly redirect to the legitimate Microsoft login page to believe it was a genuine operation.

Figure 3: Legitimate Microsoft loading page
We’ve noticed on similar phishing attempts; threat actors will redirect the victim to the above blue envelope image in Figure 3, immediately after their credentials would have been provided. This is done, so the recipient is led to believe their mailbox is loading.

Figure 4: Legitimate Microsoft login page
Malicious emails like this are becoming an ever-increasing phenomenon in business environments today and it’s imperative for companies to have a procedure in place to deal with these threats. With corporate credentials being such a high target for attackers, it’s easy for an attacker to assume that posing as a service which employees use every day will increase the number of victims affected. With Cofense tools and services, malicious emails can be identified, and indicators of compromise (IOC)’s given and shared. You and your customers can be confident that campaigns like this will be thwarted. Find out how Cofense can help you and your clients be more resilient to attack.
| Indicators of Compromise | IP |
| hXXp://eqsealvetrisrlit | 46169169 |
| hXXps://versed-hexagonal-rakeglitchme/ohk.html | 5019254224
3517219651 5220040111 18210105246 342294215 54205166180 |
Guest blog written by Jer O’Donovan and Anthony Wright & Cofense Phishing Defense Center. Read more Cofense guest blogs here. Regularly contributed guest blogs are part of MSSP Alert’s sponsorship program.




