Over the past couple of years, we’ve witnessed a rapid adoption of endpoint detection and response (EDR) in the MSP space. An increasing number of managed service providers are choosing to leave behind legacy antivirus (AV) solutions in favor of EDR security. The differences between the core functions of AV and EDR are easy to understand and many see EDR as an obvious choice. However, some still believe that AV is enough because the customers they support have a low risk profile. This overlooks the fact that the world isn’t what it used to be, and that merely being the customer of an MSP can increase the risk profile of a business.
In what follows, we’ll look at why standard AV is no longer a valid choice for MSPs and why you need to step up your game.
Reason #1. MSPs seen as main targets in today’s threat landscape
The pandemic has changed the way we conduct our daily activities. People are spending more time online—working, shopping, attending virtual events and even doctor’s appointments—pushing organizations to accelerate their move to the cloud. Add WFH and BYOD, and this all translates to increased connectivity and larger attack surfaces for individuals and businesses.
As an MSP’s role is to manage and protect their customers’ IT assets, data, and business processes, they often have broad access to those customers’ systems. This makes MSPs and the tools they use an attractive attack vector. It’s no surprise that MSPs are quickly becoming main targets for cybercriminals. A recent N-able report found that MSPs are fast becoming primary targets for cyberattacks; almost all MSPs have suffered a successful cyberattack in the past 18 months, and 90% have seen an increase in attacks since the pandemic started.
To put it bluntly, it’s not a matter of if, but when you’ll get hit. Now the real question is: How fast can you recover from an attack? This is where EDR comes in, not only to prevent attacks, but to provide the rapid recovery that AV cannot.
Reason #2. Threat incident response: Time is of the essence
Threat incidents cause downtime, which leads to lost business. The longer it takes to resolve a threat incident, the higher the costs—according to an ITIC 2021 report, 91% of enterprises registered downtime costs exceeding $300,000 per hour. So when it comes to resolving threat incidents, speed is crucial. But you’re only as fast as the solution you use.
If you’re using legacy solutions, like traditional AV, you’re at higher risk of severe business disruption than if you were using EDR. While AV and EDR share similarities in that they are designed to protect against endpoint threats, they offer different levels of protection and automation, which impact threat response speed. In fact, according to industry surveys and our security experts’ own experience, a median of the time spent on manual remediation after the AV solution catches a threat is roughly 3.5 hours. In contrast, the quality of analytical data and telemetry recorded by EDR paired with its automated remediation and additional features can reduce that time to resolution to less than 30 minutes, sometimes even as low as five minutes.
To demonstrate this, let’s put on a threat responder’s hat and imagine we’re experiencing a malware attack. To keep things simple, we’ll consider a malware attack that any security solution can catch, and we’ll look at how a threat incident response timeline would unfold using AV for one scenario, and EDR for another.
Scenario 1: Threat incident response timeline using AV
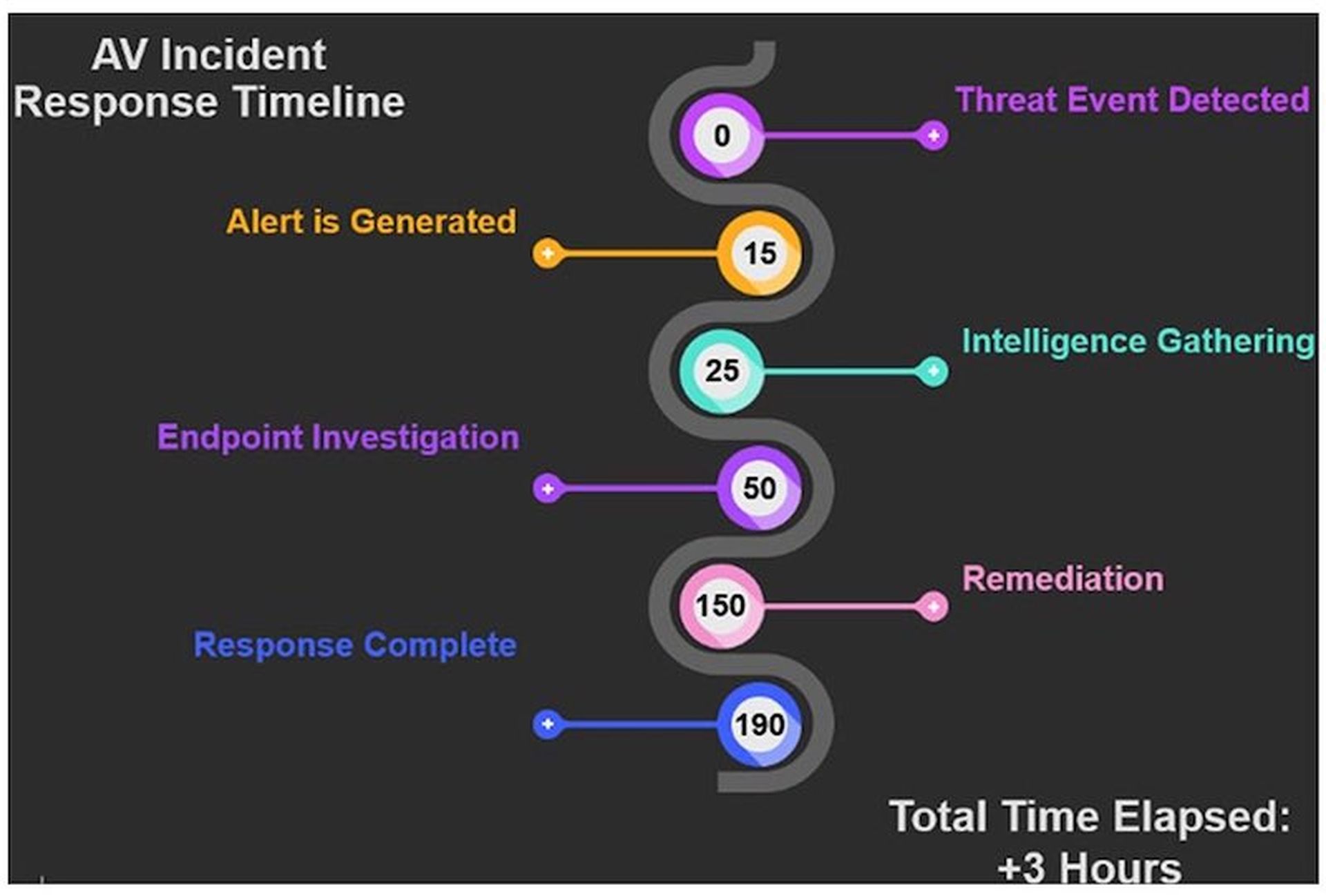
- Step 1. Threat event detected: The AV solution detects and stops the malware event.
- Step 2. Alert generated: Within 15 minutes, alerts and ticket workflows should notify a responder.
- Step 3. Intelligence gathering: Next, the responder has to gather threat intelligence to establish an adequate response. This is usually limited to time, drive location, threat descriptor name, and action taken retrieved from the AV dashboard.
- Step 4. Endpoint investigation: Due to limited intelligence available in the AV dashboard, the responder must manually investigate the health of the endpoint and may discover misconfigurations or other unwanted behavior introduced by the malware.
- Step 5. Remediation: Many responders will not have time or access to solutions that could help them truly understand what happened to the endpoint during the threat event. So, they will revert to “spray and pray” in the form of repair tools, cleanup utilities, system restores and re-running malware scans, etc.
- Step 6. Response complete: Once there are no longer any surface level indicators of persistent issues on the endpoint, the responder will consider the incident resolved; however, they will unlikely be able to fully validate everything has been remediated. Instead, they, at some point, will have to just say “good enough”.
Typically, by that time, more than three hours would have passed.
Scenario 2: Threat incident response timeline using EDR

- Step 1. Threat event detected: The EDR solution detects the malware event on the endpoint.
- Step 2. Remediation: The threat is killed and quarantined with remediations to undo any damage done to the system. This is done automatically, sometimes within seconds.
- Step 3. Event reported in the dashboard: Within minutes, alerts and ticket workflows should notify a responder.
- Step 4. Intelligence gathering: Detailed information about the threat event is available in the dashboard for the responder to review, such as time, locations, full timeline of processes, system registry changes, and other valuable analytical data about the threat.
- Step 5. Response complete: Next, the responder creates the incident report and closes the ticket. Thanks to the automatic remediation capabilities and the availability of detailed forensic information, the threat response is typically complete in less than 30 minutes. At the same time, the responder can have greater confidence that any modifications made to the system have been remediated. Since EDR is designed to recognize this threat via its hash value, any future exposure to this threat should be detected by the static-engines in EDR, preventing this particular threat from ever executing again.
If, now that we’ve looked at the more practical side of things, you’re still leaning towards legacy security solutions, consider what the cybersecurity future holds. How prepared are you for it?
Reason #3: Further security innovations on the horizon
To better support remote work and enhance customer experiences, companies are adding more systems in their IT networks to deliver those new services, which creates new vulnerabilities. This inevitably raises the question of whether they are properly equipped for the increasingly digitalized future.
McKinsey research shows that many organizations recognize the need to strengthen their cybersecurity capabilities and to ensure the resilience of their technology. The solution that McKinsey recommends is for companies “to reinforce their defenses by looking forward—anticipating the emerging cyberthreats of the future and understanding the slew of new defensive capabilities that companies can use today and others they can plan to use tomorrow.”
Along the same lines, in a recent N-able webcast, Chris Krebs, former CISA director, makes an important observation: “Attackers are also rational, economic actors, looking to get into the supply chain to launch a one-to-many breakout attack. They are going to use the same techniques until these won’t work anymore. You want to put yourself in that space where their techniques don’t work on you anymore, and they’re going to shift their focus away from you. Which is why we need to continue improving our defenses and the bad guys will move down the value chain on attacks. There’s still room for improving our defenses.” So, if you think of cybercrime gangs and APT groups as business owners, anticipating their next moves may not be such a heavy-lifting task after all.
One thing is clear: As cyberthreats continue to increase, so too will cybersecurity spend. We’ll see more investments in AI and machine-learning to keep abreast of changing attack patterns, as well as automation capabilities to streamline automatic responses to attacks. Solutions like EDR and XDR already offer these types of innovations, and they will continue to evolve to not only counter but outpace attackers.
To stay in the game, you will want to improve your defenses against tomorrow’s threats, not just today’s. As MSPs are becoming more attractive targets for cyberattacks, it’s important they move away from legacy solutions and help future-proof their defenses.
“If you want to learn more about the current threat landscape, how an attack chain works for threats today, and the security solutions that MSPs can employ to help future-proof their defenses, check out the bootcamps, blogs, and other resources in the N-able Security Center.”
N-able EDR offers 100% protection and detection, highest visibility and analytic coverage, and 100% real time, zero detection delay. To find out more click here.
Emma Nistor is senior product marketing manager, N-able EDR. Read more N-able guest blogs here. Regularly contributed guest blogs are part of MSSP Alert’s sponsorship program.




