New technologies such as containerized applications are driving innovation and productivity like never before, but with these advancements come some concerns. Today’s attacks move fast, often in seconds rather than minutes or hours, and leave little time for incident responders to prevent the damage from data breaches, tampering and disruption.
According to 451 Research, half of enterprise organizations are either using containers today or planning to use them in the next two years. The research firm reports that “growth in the containers market and ecosystem is being driven by increasing enterprise interest to help application developers move faster, manage infrastructure more efficiently and meet digital transformation goals.”
That’s great, but containers need to be secured along with the applications within them and their production infrastructure. If malware gets on your clients’ containerized apps within their corporate IT network, it can move laterally throughout the organization, even infiltrating the OT network (and vice versa). It could be an executable or memory-based malware, a drive-by browser download, phishing or exploit-related, document exploit or script. It doesn’t matter. If any of their containerized apps are compromised, they can experience data loss, data corruption and interruptions to business availability and production, to name a few.
Automation helps security and operations teams predict, mitigate, prevent, detect, contain and remediate fast-moving attacks while controlling the costs of scarce staff resources often overwhelmed by the complexity and volume of threats, which now extend to containerized environments. You should look for a solution to discover containerized applications, manage communications between them and manage and enforce policies in containerized environments. This should include vulnerability assessment and virtual patching (which also extends to native apps). Here’s what that looks like:
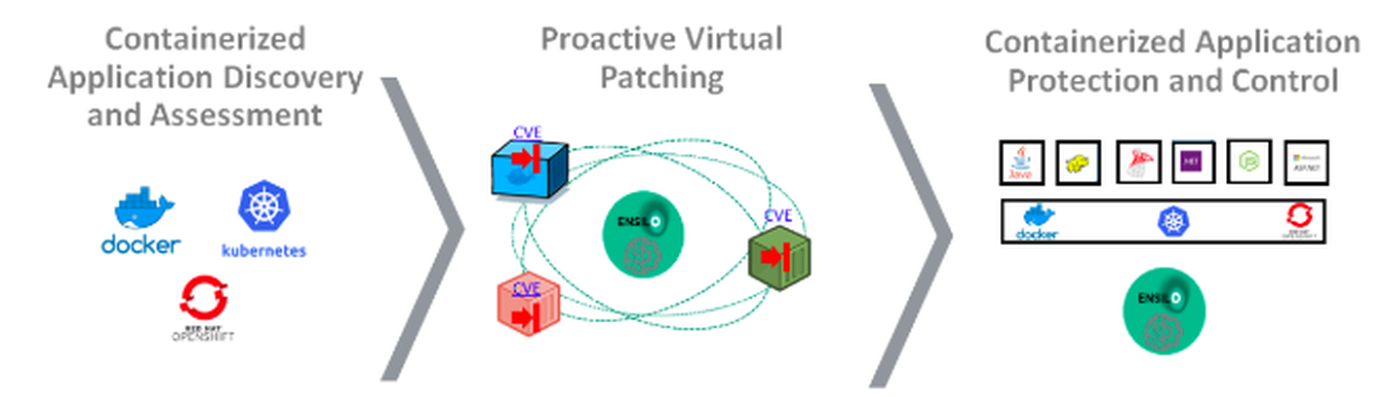
- Discover containerized applications and audit-related activities.
- Reduce the attack surface through communication control policies constructed with application reputation score and correlated with CVE data to proactively block specific versions communication upon any device.
- Control privileged container accessibility, running instances coherency and cluster(s) accessibility.
How enSilo Can Help
With enSilo’s version 4.0, visibility into and protection of containerized applications will be part of our advanced endpoint security platform. We achieve this by using endpoints already deployed with the enSilo security stack, therefore reducing the number of consoles and solutions needed to get a full understanding of what's on the network.
enSilo’s discovery, vulnerability assessment and mitigation capabilities add a critical layer of network security protection to customers’ already existing real-time pre- and post-execution protection from enSilo, which includes:
- Real-time prevention featuring kernel-based next-generation AV for automated prevention of ransomware encryption. enSilo incorporates machine learning so it becomes smarter over time and draws from a continuously updated cloud-based threat intelligence feed. Real-time prevention is pre-infection, and just good sense when it comes to security hygiene.
- Real-time detection and containment featuring automated endpoint detection and response, including post-infection detection and blocking for surgical containment of threats.
- Real-time orchestrated incident response with automated event classification, automated remediation and automated investigation without interrupting the user.
With enSilo, you can strategically reduce attack surface complexity and costs in the extended enterprise. In doing so, you’ll minimize incident response time pressures on clients while also preventing vulnerability exploitation that commonly leads to data breaches and the disruption caused by cyberattacks. If you’d like to learn more, please sign up for a demo today.
Roy Katmor is CEO and co-founder of enSilo, an endpoint security platform provider. Read more enSilo blogs here.




