Ransomware has made a resurgence and is impacting both IT service providers and the businesses they serve. What if you had insights into cyber criminal tactics and techniques happening in your environment? What if you knew more about the adversaries you face in this cyber battle? Can you help your customers prioritize potential threats to stop a ransomware attack before it’s too late? The MITRE ATT&CK framework enables service providers and defenders to optimize protection beyond legacy tools like anti-virus.
MITRE ATT&CK Recap

As a summary, MITRE launched ATT&CK (Adversarial Tactics, Techniques, and Common Knowledge) to document and globally share adversary behavior in a practical way. Benefits of the ATT&CK framework include:
Adversaries often re-use the same techniques that they understand and have found successful, enabling defenders like you to help predict, prevent, detect, and rapidly respond to advanced threats.
“ Offense is the best driver for cybersecurity defense.”
- The MITRE Corporation
Today, many organizations are using ATT&CK to better plan and prepare against advanced threats like ransomware.
Prepare for Ransomware Analysis and Detection
The ATT&CK framework provides a common language for threat analysts to use when describing analyst behavior. This common threat terminology helps with consistent and clear communication within your MSP organization as well as across world-wide threat-sharing entities. Cybersecurity decision making also improves when ATT&CK is integrated with Security Information and Event Management (SIEM) such as Netsurion’s threat protection platform. The TTPs in ATT&CK have their foundation in network, application, and infrastructure systems and logs, making SIEM correlation and threat analytics even more useful.
Understand Your Current Defenses to Close Ransomware Gaps
ATT&CK is based on actual tactics, techniques, and procedures (TTPs) used in real-world threat campaigns like ransomware. ATT&CK also provides details on 100+ threat actor groups across the adversary lifecycle, from Reconnaissance to Action on Objectives as Diagram 1 shows. Defenders are often challenged to find that many ATT&CK techniques include legitimate system functions used for malicious purposes, making quick detection of cyber criminals even more crucial. While implementing ATT&CK on your own can be resource intensive and time-consuming, solutions such as Netsurion’s Managed Threat Protection integrates the ATT&CK framework so that you don’t have to. You now have the same cyber criminal TTPs and threat context as organizations with much larger security teams.
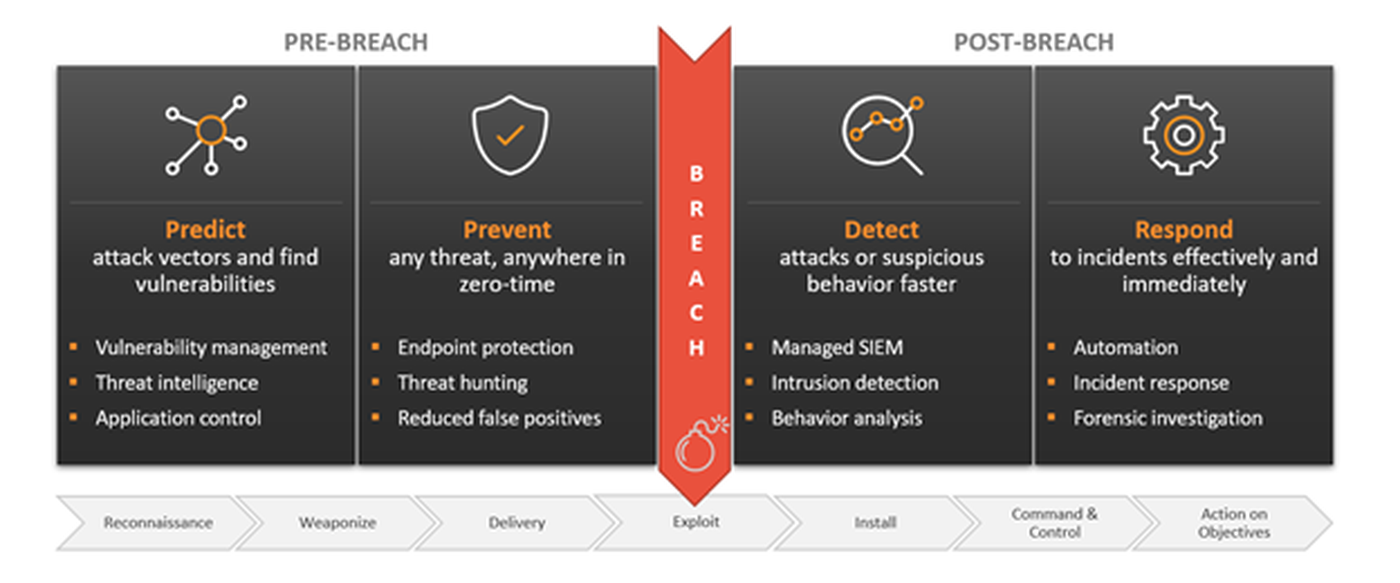
Diagram 1: Comprehensive cybersecurity protection across the threat lifecycle is enhanced significantly when MITRE ATT&CK is properly integrated.
Continue to Evolve your Security Posture
The ATT&CK framework is immediately usable in IT environments for MSPs and their end customers. As adversaries morph their nefarious techniques, so too does MITRE as it adapts and updates the ATT&CK cyber threat intelligence and TTPs. The framework has expanded over time to address cloud and mobile technologies. Your valued customers trust you with their data and reputation; adopting the MITRE ATT&CK framework ensures that you don’t fall behind when it comes to protecting business-critical data and maintaining customer uptime.
Optimize your Protection with MITRE ATT&CK Integration
Organizations of all sizes use ATT&CK to better address the evolving threat landscape. In fact, MSPs are now ransomware targets due to their pervasive supply chain connectivity and penchant for ransom payments to avoid negative publicity. Faster response minimizes dwell time, the dangerous time hackers spend in an organization’s infrastructure performing reconnaissance and doing damage. Integration of ATT&CK with SIEM log correlation and data analytics provides single-pane-of-glass visibility and improved decision making.
Conclusion: Leverage a Layered Defense
MITRE’s ATT&CK framework outlines what known attackers do when they enter your network. We seamlessly integrate ATT&CK with a managed service that predicts, prevents, detects, and rapidly responds to ransomware and other cybersecurity incidents. This defense-in-depth approach strengthens cybersecurity at all stages of the attack lifecycle, from pre-breach to post-breach. Learn more about Netsurion’s Managed Threat Protection and ATT&CK integration to create a proactive defense for MSPs and their end customers when every minute matters.
Author Paula Rhea, CISSP, is product marketing manager, Netsurion. which develops the EventTracker Managed Threat Protection platform for MSSP and MSP partners. Read more Netsurion guest blogs here.




