The term "boom" is used to describe the moment of breach -- the actual time when a cyberattack, intrusion or some other form of incident succeeds.
At its core, according to Cyderes CTO Tim Malcom Vetter:
A “boom” or “bang” is an unwanted, bad event for the defender — the initial contact from the offender. “Left of boom” is the set of events that occur in the timeline before the boom and “right of boom” is the set of events that follows. Very simple."
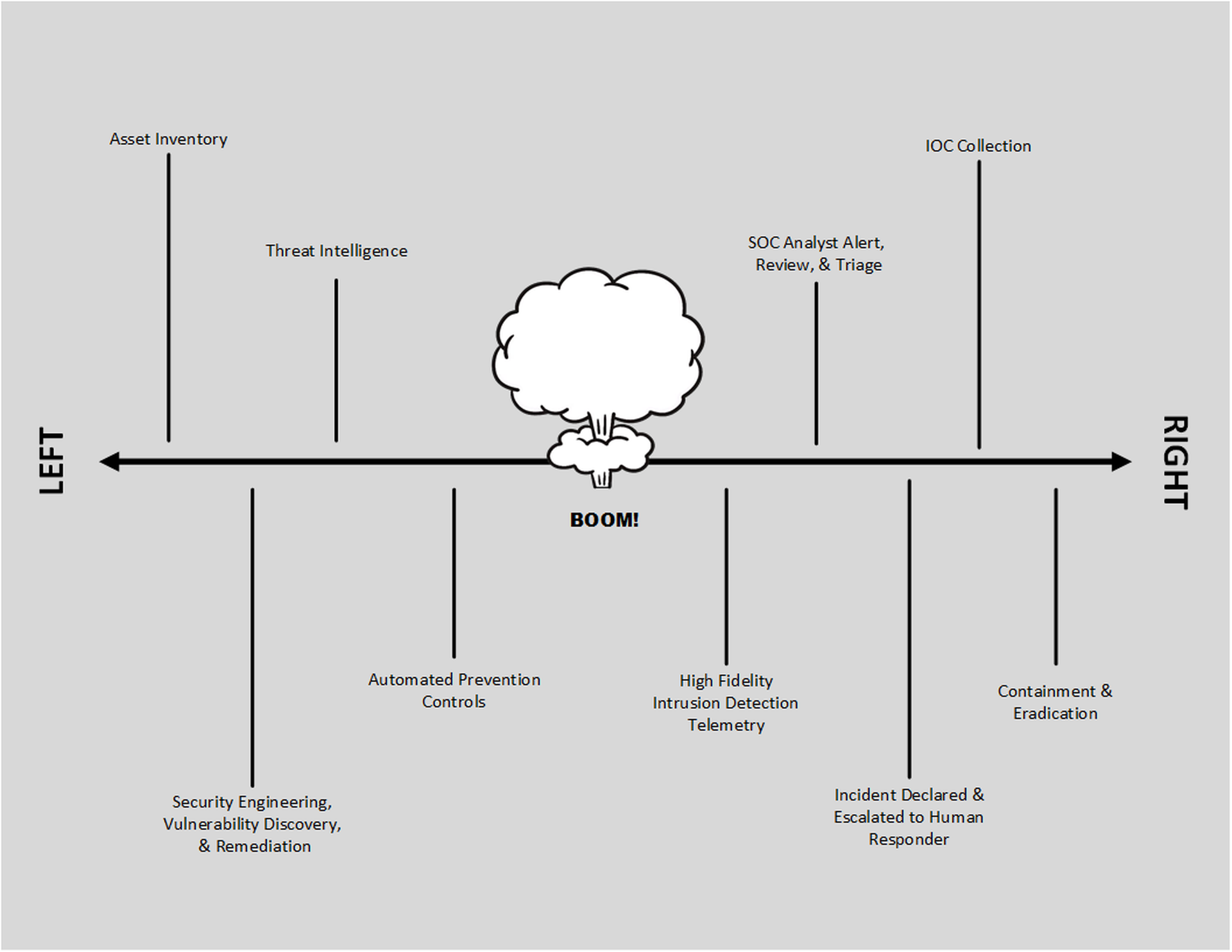
Yes, the definition is simple. But everything an MSP does during the Right of Boom could decide a service provider's business fate -- and the fate of the MSP's end-customer interactions.
Right of Boom: How Do Smart MSPs Navigate Security Incidents?

I concede, the terminology above is fairly new to me. And I have to give credit where credit is due: Andrew Morgan, founder of The Cyber Nation, first mentioned the Right of Boom concept to me sometime in mid- to late-2021. Turns out, he was planning an MSP-focused conference aptly named Right of Boom. It's set for February 9-11, 2022 in Tampa, Florida.
And yes, I plan to attend. Why? The simple answer involves my search for best practices in managed detection and response (MDR) -- particularly the R. Everyone seems to be jumping on the MDR bandwagon these days. I understand how automation is further improving managed detection. But frankly, I'm still skeptical about many automated Response market claims. And moreover, I believe many MSPs lack formalized incident response plans -- documented processes that could save their businesses and customer businesses after an incident occurs.
Let's go back to the example graphic above from Malcom Vetter. In his greatly simplified example, navigating the Right of Boom involves such tasks as:
"Everyone Has a Plan, Until..."
Those are great high-level starting points for an incident response plan. But to paraphrase Mike Tyson: Every MSP has a plan until they get punched in the mouth by a cyberattack. So how can MSPs go deeper and build plans that truly keep their businesses -- and their customer businesses -- online despite attacks and other compromises? I'll be hunting for answers during the Right of Boom conference in Tampa. If you'd like to meet me there, please email me: Joe.Panettieri@CyberRiskAlliance.com and include the subject line "Right of Boom Meeting Request."
See you there.




